British shoppers have been warned to expect some of their favorite snacks to be in short supply following a ransomware attack on a major manufacturer.
KP Snacks has been producing snacks in Britain since the 1850s, but this production has recently run into a major obstacle: ransomware. Cyber criminals have successfully launched a ransomware attack on KP Snacks, and its effects are running deep. Due to the impact of the ransomware on their IT infrastructures, KP Snacks has had to advise stores that delays in production are expected. As a result, British shoppers are likely to be facing empty shelves when they head out to pick up their favorite snacks.
Snack food may not be crucial to society, but the impacts of this hack demonstrate why organizations need to remain vigilant.
The Story Behind the Snack Attack
Following an unexplained outage of their IT systems, KP Snacks investigated and discovered that they had fallen victim to a strain of ransomware. The exact details of the ransomware in question has not, as of yet, been disclosed. However, rumors are circulating that the attack was launched by the WizardSpider group, a gang of hackers who attacked the Irish health service in 2021. It’s alleged, according to leaked sources, that KP Snacks was given five days to pay a ransom fee, but clarification on this is lacking.
The response of KP Snacks has been to launch a defensive strike against the attack. Being a major organization, the snack makers had a cybersecurity response plan which was quickly put into action. Third-party security experts have also been drafted in to complete a forensic analysis of the firm’s IT infrastructure. Nonetheless, the disruption to productivity has hit KP Snacks hard. As well as their IT systems being compromised, their communications systems have been hit equally hard. In modern business, these two elements are essential for operating and, as a result, supply shortages are expected.
Protecting Yourself Against Ransomware
While a shortage of snacks may sound like a mild inconvenience, this is only the tip of the iceberg. Not only is there a financial risk for KP Snacks, but the company’s employees can also expect financial ramifications e.g. delayed payments due to compromised IT systems and even the threat of redundancy. Naturally, this is a situation that no organization wants to find itself in, so make sure you always follow this advice:
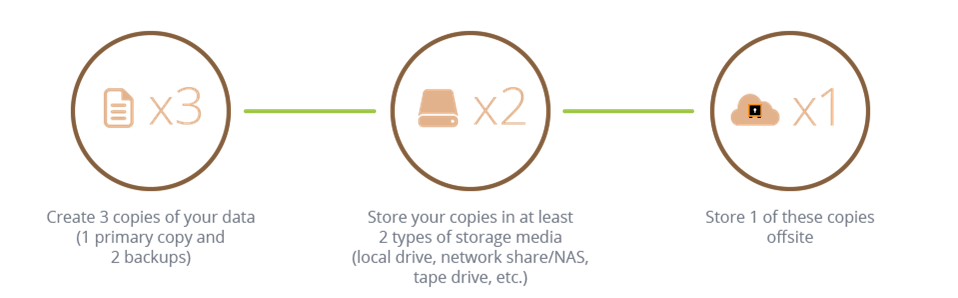
- Always Backup: the main impact of ransomware is that it encrypts files before demanding a ransom fee to decrypt them. However, you can minimize the impact of this effect by ensuring you have a strong backup strategy in place. This will provide you with access to your data and provide you with business continuity.
- User Training: ransomware can be activated in a number of different ways such as infected emails, malicious links and running outdated software. Thankfully, shutting these attack routes down is relatively easy with the correct training. Therefore, regular staff training is vital when it comes to securing your IT defenses.
- Install Anti-Malware Tools: it’s almost impossible to detect every single threat in the digital wild, but anti-malware tools will protect you from most of them. Installing anti-malware tools is simple and instantly provides an enhanced level of protection against ransomware.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More