Do you know what to do when your printer stops working? If not, we’ll help you take out some of the guesswork with some basic troubleshooting tips.
Printers may be an understated piece of equipment. It almost becomes part of the office furniture, until it gets used for printing. But what happens when the office printer stops working, what is one to do before they decide to call for help? Firstly, remain calm. The good news is that we’ve pieced together a checklist for what to do when a printer stops working.
What to check before first
Just a preliminary note: It may sound obvious; however, most printers can actually display the problem on their LCD displays or give clues as to what the problem is. Make a note of any errors which may flash on this display too.
- Restart the printer. Simply power off and then switch it back on. Sometimes all that is needed for a printer to work well again is a simple restart. This often does the trick, almost works like magic!
- Clear the printer’s sprint queue. This is a common problem where one print job within the print queue jams up all other print jobs waiting for their turn to print in the queue. To clear the queue, simply head over to the printer’s setting from your computer’s Control Panel on Windows 7 or 8 by going to
Start > Control Panel > Hardware and Sound> Printers
Double click the printer that has the problem.
A print queue should be available, and from there you can delete and clear the print jobs to tell it to stop printing. Click Cancel to remove the print jobs.
Try to send a new print job to test its working fine.
- Make sure your printer has enough supplies. By this we mean enough paper to feed through it and plenty of ink to use. Insufficient levels of these can make a printer unhappy, so be sure to not overlook this!
Paper Jams- a common problem

Printers are usually good at telling their users when there’s a paper jam. If there is one, it’s a good idea to check that paper isn’t stuck. Even the smallest piece of paper jammed in the printer’s rollers qualifies as a paper jam.
Sometimes a printer will complain about a phantom paper jam. In this case, it’s a matter of checking there’s enough paper in the paper tray and all trays or doors are closed shut.
Servicing your printer
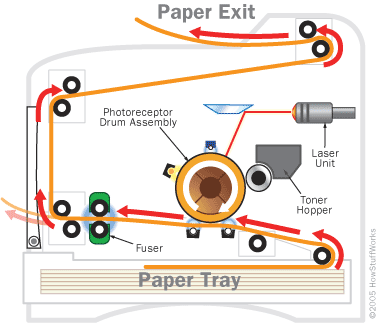
Diagram of the inside of a typical laser printer from Zinetic.
Laser jet printers need servicing from time to time, so it’s always a good idea to have it serviced. Once a certain amount of printing threshold has been reached, the printer may request a service to replace one of its components from wear and tear such as a print drum or paper roller, helping to further extend the printer’s life.
Check the warranty
It’s always a good idea to register your printer for its warranty as soon as it arrives in the office. You’ll want the least amount of trouble by having your warranty activated which will cover you for a faulty printer and have the problem fixed promptly by the vendor.
For more ways to troubleshoot your printers and computers, contact your local IT professionals.
Read More