Google Fiber promises super fast broadband, but it remains out of reach for many people. However, it now looks as though it will shortly debut in San Jose.
The days of conducting business over a 56k dial up modem seem like a lifetime ago and in the last decade the speed offered by broadband has rapidly increased. It may seem as though it can’t get any quicker, but believe me it can! And it’s all thanks to ‘gigabit internet’ services.
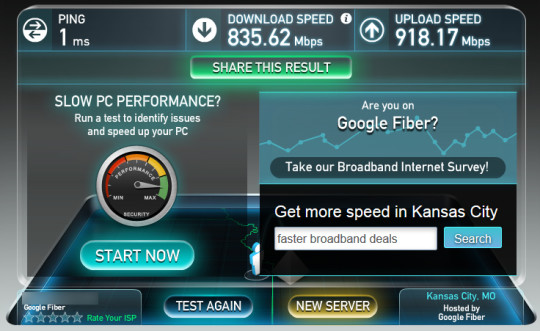
Google, always at the forefront of internet technology, has been working on Google Fiber for the last 5 years and it promises a huge connection speed of 1,000 megabits per second. Despite first launching in 2011 expansion has been slow, but it’s strongly rumored that it’s debut in California will be in San Jose.
Let’s take a look at exactly what’s known about this launch and what it means for your business!
The Rumors Behind San Jose’s Launch
Despite there being no official announcement over Google Fiber’s expansion into San Jose there remains many indicators that it’s almost a done deal.
Perhaps the biggest shred of evidence is that Google has already got the ball rolling by applying for planning permission to construct two ‘Fiber Huts’ – these buildings house all the fiber optic equipment necessary to provide the regional network with gigabit access. And there are also proposals to build a further 8 in the city which would indicate a very strong drive to make Google Fiber a viable option.
Google has been discussing their plans for Google Fiber with city officials for some time now, but it had been difficult to reach a compromise. As a result, the discussions had broken down on at least two occasions leaving the move in jeopardy. However, it appears that progress has been made and the noises from City Hall point towards an announcement towards the end of November.
Why Will Google Fiber Be a Big Deal?
Google Fiber, then, seems to be on its way to San Jose, but what benefits is this going to bring to businesses in the city?
- It will far outstrip the services currently provided in the area. At present the quickest internet service offered in San Jose is 250 megabits through Comcast.
- The speed offered by Google Fiber will make cloud computing more viable due to the increases in accessibility and speed of available cloud services.
- Video conferencing will become more accessible and will increase the potential for workers to work from home and connect with geographically separated colleagues like never before.
Google Fiber Is Only a Matter of Time
Google Fiber in San Jose feels as though it’s only a matter of time and I wouldn’t be surprised to see it launch in 2016. And if it does then it’s going to be incredibly exciting for the residents and businesses in the city. The potential to improve their digital lives is huge and promises to make dramatic changes to the way we do business.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More