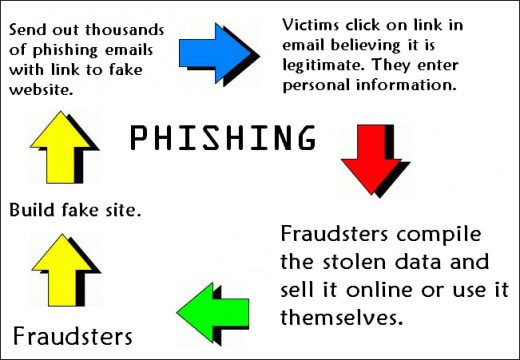
Ransomware continues to cause chaos for organizations with the latest story to hit the news concerning a Scottish brewery infected by the Dharma ransomware.
While it has been reported that ransomware attacks have fallen by 30% in the last 12 months, the fact remains that they’re still capable of causing significant disruption. In the case of the Arran Brewery on the Isle of Arran, Scotland, the organization had to accept that they would lose around three months’ worth of sales data due to the effects of the attack. This, of course, is the last thing that any business wants and acts as a fine reminder that we need to be on guard against ransomware.
To help provide a little background and demonstrate how the attack unfolded, we’re going to take a closer look at what happened.
Attacking the Brewery
What’s most interesting about the attack on the Arran Brewery is that it would appear the attackers deliberately targeted the brewery. Instead of a scattershot approach which targeted multiple organizations, the hackers focus was clearly on the Arran Brewery. Just before the attack, multiple adverts for a job at the Arran Brewery (which had already been filled) appeared on recruitment sites all over the globe. Naturally, the brewery received a sharp increase in the number of CVs being emailed in but, unfortunately, one of the emails contained a malicious payload.
The payload was contained with a PDF attachment which, when opened, initiated the attack and infected the entire network. Following the encryption of the Arran Brewery’s files, a ransom demand was issued which advised that the encryption keys would only be released in exchange for 2 bitcoin (roughly $14,000). Thankfully, an IT consultant was able to retrieve a significant amount of the encrypted data from backups and rid the system of the infection. However, certain files couldn’t be restored and, due to it not being economically viable to pay the ransom, the Arran Brewery decided to write off three months’ worth of sales data.
What is Dharma?
Dharma is a strain of ransomware which was first released in 2016 and has regularly been updated ever since due to the emergence of Dharma decryptors. In September 2018, for example, three new variants emerged which are resistant to previous decryptors. When files are encrypted by Dharma they will automatically append a new file extension onto the existing file and these extensions can include:
- .dharma
- .cesar
- .onion
- .wallet
- .zzzzz
Final Thoughts
If anything acts as a reminder that organizations need to be vigilant against ransomware then it’s a current and contemporary threat. Dharma could easily hit your organization next, so you need to ask yourself whether you can afford to lose three months’ worth of data. I’ll let you into a little secret: no one wants to lose three months’ worth of data. Therefore, it’s crucial that you reiterate the importance of email security to your employees in order to maintain access to all your data at all times.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More