Phishing is big business for hackers and you can rest assured that it’s a niche they’re keen to exploit, but how do you know when you’re being phished?
Kaspersky Lab reported around 246 million phishing attempts being executed in 2017, so it’s fairly clear that phishing is taking place on a monumental scale. And, to provide a little perspective, those 246 million phishing attempts are only the ones that were picked up by Kaspersky’s software. If you factor in all the other security providers’ data then you’re left with a staggering amount.
Phishing, therefore, is something that you’re likely to encounter and, the truth is, your organization is likely to receive a significant number of phishing emails every day. Thankfully, protecting your business from the dangers of phishing emails is relatively easy. And, to help boost your defenses, we’re going to show you four ways to tell if you’re being phished.
1. Analyze the Email Address
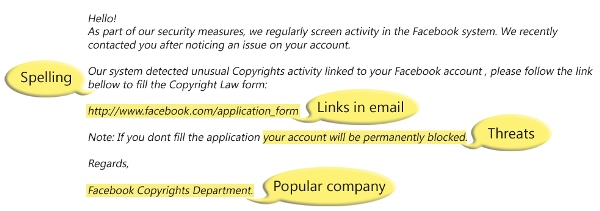
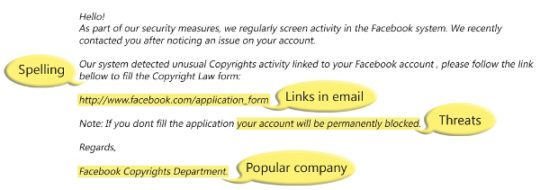
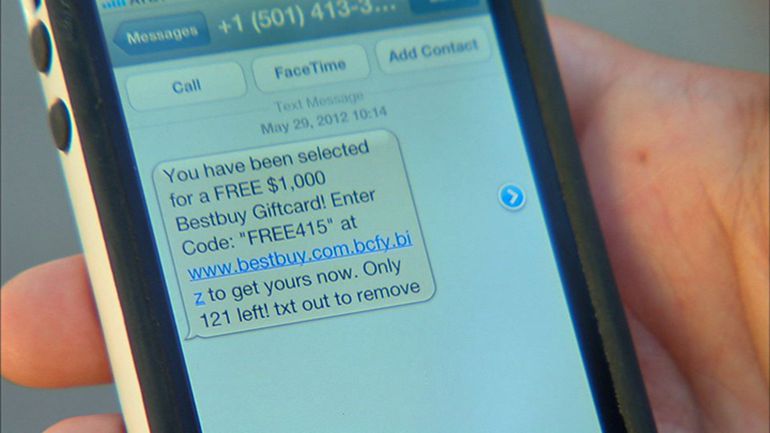
While it’s straightforward to mask an email address with a false one, many hackers simply don’t bother. And that’s why you’re likely to find that most phishing emails are sent from unusual email addresses. Say, for example, you receive an email from your bank asking you to provide sensitive information regarding your account, it’s not going to come from a Hotmail address, is it? However, many people fail to check the sender’s email address and, instead, become distracted by the seemingly genuine contents.
2. How’s the Grammar?
A tell-tale sign of a phishing email is poor grammar and even worse spelling. Hackers, after all, aren’t too bothered about honing their command of the written word. All they want to do is hack and hack big. Accordingly, their emails will fail to contain the type of language you would expect to receive from a work colleague or another organization. So, remember: if they can’t spell your name in their opening introduction then you should be highly suspicious.
3. Did You Ask For Those Attachments?
Hackers love to catch their victims out with attachments that contain a nasty payload, so any attachments should always be treated with caution. Sometimes these attachments can be easily identified as malicious, but it’s not always simple. First of all, ask yourself whether the attachment is relevant to your job. If you work in the service department and you’ve been sent a spreadsheet relating to company finances then there’s no need for you to open it. Secondly, keep an eye out for file extensions you don’t recognize as opening these could easily lead to executing malware.
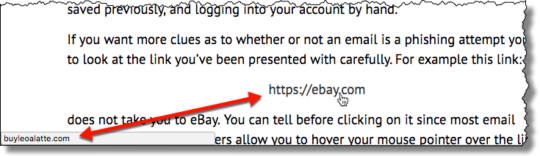
4. Deceptive Links
One of the main objectives of a phishing email is to take the recipient away from the security of their PC and onto dangerous websites which are riddled with malware. And the best way they can do this is through the use of a deceptive link. While a link may look genuine on the surface, it can easily direct you somewhere else altogether. The best way to verify a link’s true destination is by hovering your mouse cursor over the link to reveal the true URL address.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More