We like to think that once a cyber-attack takes place that a solution will be found. However, malware is evolving and becoming harder and harder to stop.
In Q1 2016, Kaspersky prevented just over 228 million malware attacks and this is a figure which has been increasingly rapidly for the last few years. In fact, several years ago, it would have been unlikely to see pushed 228 million malware attacks in an entire year.
Malware, therefore, remains big business for hackers so, naturally, they’re constantly looking to upgrade their weaponry to beat the firewalls and antivirus software we rely on. And it’s a digital arms race which the cyber security experts are struggling to keep up with.
Let’s take a look at why malware is getting harder to stop.
Ransomware Arrives

One of the most reported evolutions in the malware landscape has been the rise in ransomware attacks such as Locky.
Ransomware is a form of malware which encrypts users’ files and then demands a ransom to decrypt them. Being a relatively new form of malware, knowledge regarding their build and execution capabilities is somewhat limited, so this is making them particularly difficult to combat.
What’s also crucial to the success of ransomware is that the majority of attacks are routed through anonymous Tor servers which mask the attacker’s true IP address. This means that identifying the hackers becomes very difficult and they’re able to continue operating impeded and improve their malware. And this evolution of existing ransomware is best demonstrated by the Locky Trojan which began as a .DOC file, but is now being identified as a .ZIP archive in order to evade detection.
Targeted Attacks
Malware has, traditionally, followed the same execution regardless of which network it has been deployed upon. However, hacking groups such as Poseidon are now ensuring that their attacks are, after the standard breach, able to customize the attack depending upon the network.
Poseidon maps their victims’ networks and harvests all the available credentials to ensure they can gain the maximum privileges on the network. And the reason for this customized attack is because Poseidon is actively hunting the computer which operates as the local Windows domain controller. If the hackers are able to take control of this computer then they will have free rein over the entire network.
It’s this type of attack which is a cyber-security firm’s worst nightmare as it involves extensive research into the intricacies of individual networks. This is very time consuming and underlines how hackers are actively looking to make themselves more powerful.
Long Term Evolution
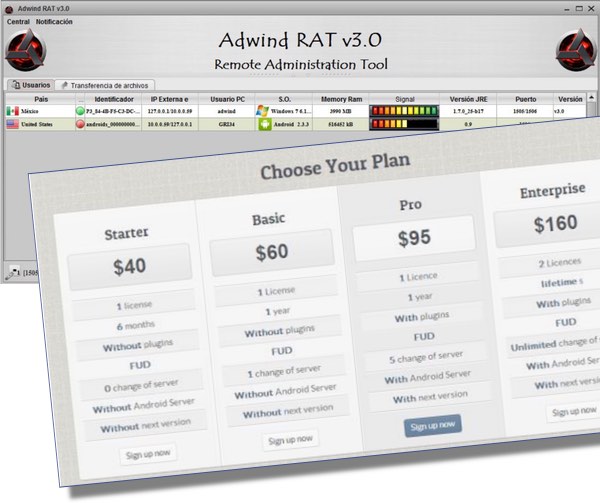
One of the biggest problems with Malware is that certain strains are constantly evolving into new strains. The best example of this is the Adwind RAT (remote access tool) which first appeared in 2012 as a tool for online spying.
Originally debuting under the name Frutas, it evolved into Adwind, Unrecom, AlienSpy and JSocket over the next three years. Starting off as a Spanish language piece of software, it soon received an English language interface which allowed it to spread worldwide.
All these changes have allowed the Adwind RAT to enjoy a long career and cause so many cyber-attacks. By actively changing its exterior appearance and name, it has fooled firewalls and antivirus software to leave security experts scratching their heads.
For more ways to secure and optimize your business technology, contact your local IT professionals.