You’ve read the headlines and you may even have been a victim of phishing, but what is it and how does it work?
Phishing is a highly dangerous form of hacking which can compromise sensitive data and cause significant disruption to the running of a business. One of the main reasons that phishing has become such a successful method of wreaking digital havoc is down to a lack of knowledge on the behalf of PC users. While phishing is far from the most complex hacking technique, the average PC user is unlikely to know the ins and outs of phishing.
As we know that time and productivity is a valuable asset for your organization, we’re going to take a look at the basics of how phishing works.
What is Phishing?
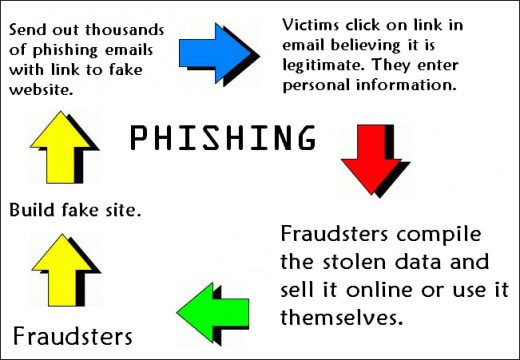
Let’s get one thing straight, phishing is nothing like sitting by a lake and peacefully fishing. In fact, it’s far from enjoyable, but there is one element that remains the same. And that’s the use of bait. You see, phishing thrives upon the use of bait to obtain information out of an innocent party. The most common way to phish, in the digital landscape, is through an email. And, within this email, will be a piece of bait with which the hackers plan to land a prize catch.
Leaving the world of fishing behind, a phishing email is one which uses a number of deceptive techniques to extract sensitive data such as login details, bank details or even secure data such as customer database spreadsheets etc. Essentially, phishing is one big con and, as with all cons, gaining the trust of the victim is crucial to success. That’s why hackers are so keen to appear genuine when they send their phishing emails.
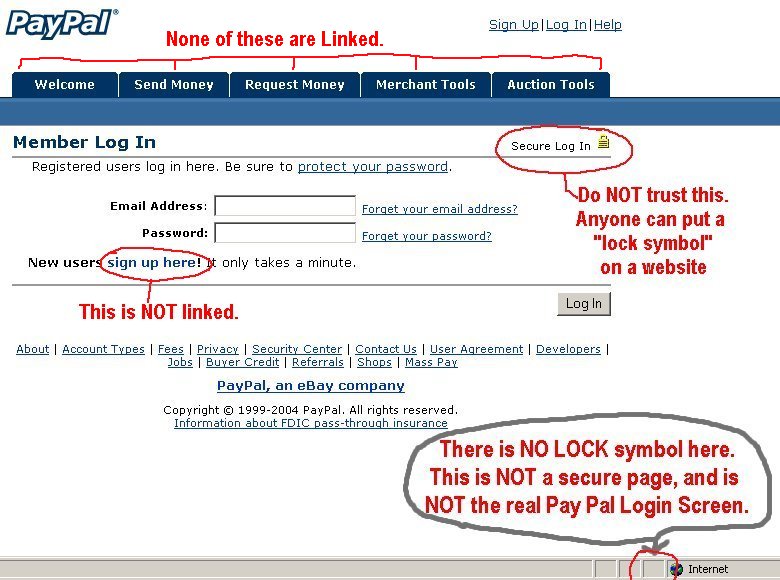
The classic example of a phishing email is one that claims to have been sent from a bank to verify your login details. A scare tactic will usually be employed, such as a report of unusual activity on the account, in order to encourage a swift response which foregoes any rational thought. A link will be included in the email which the user is advised to click in order to go through a series of security checks. However, clicking this link will take you to a malicious website – even if it looks genuine – where your data will be harvested to help fuel identity theft or, in extreme cases, a loss of funds.
Why Does Phishing Work?
You may be wondering why people fall for phishing scams and the simple truth is that it’s down to a lack of concentration and analysis. Phishing takes advantage of these weaknesses on both individuals and security software. By planting a seed of trust, such as promising to safeguard your personal data, the hacker can, in fact, do the complete opposite and use this trust to harm you.
Key to successful phishing emails is the use of social engineering to convince recipients that the emails are genuine. Phishing emails will be packed full of official company logos and it’s even possible for hackers to spoof official email addresses in the From: section of an email. And, for people busy at work, it’s easy for them to take their eye off the ball for just a fraction of a second. As a result, links are clicked that shouldn’t be clicked and hackers land their prize catch.
For more ways to secure and optimize your business technology, contact your local IT professionals.