Phishing attacks have long been a concern for anyone using computers, but a recent report has highlighted how these attacks have now risen by 250%.
Compiled by the Anti-Phishing Working Group (APWG), the report states that, during Q1 2016, there were nearly 290,000 active phishing sites online. This may not sound huge considering that there are around a billion websites online, but this is the highest number of phishing sites online since records began in 2004.
Phishing, therefore, is a credible and growing threat, so I think its best we get up to date with what phishing is and how these attacks are taking place.
What is Phishing?
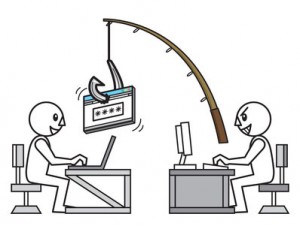 Phishing is the process of stealing personal information (login details, credit card details etc) from consumers through the following methods:
Phishing is the process of stealing personal information (login details, credit card details etc) from consumers through the following methods:
- Social Engineering – This is perhaps the most well-known method for extracting sensitive information from individuals. Using emails which convincingly spoof official emails, from corporations such as banks, they use disguised links to send victims to fake sites which contain features such as login screens. Obviously, these are false and simply record login credentials which can then be executed on the genuine site by the phishers.
- Technical Subterfuge – This method employs the use of crimeware which is a type of software that hides in the background and records sensitive information such as login credentials. Also, many crimeware kits hijack users’ browsers to redirect them to phishing sites where the users unwittingly provide personal information.
What Does the Report Show?
A number of interesting insights have been provided by APWG’s report, so let’s take a look at these to understand how they unfold:
- The most infected country is China where 57% of all computers are infected with malware. Considering how productive China is, at present, this makes for an alarming statistic as it’s likely that any business involved in production will be receiving emails containing crimeware from China on a regular basis.
- Around 77% of all phishing websites are based in the US and the majority of these are forcibly set up by phishers who break into web hosting networks. This highlights major security flaws in US web hosting networks which is of particular concern for US businesses who own a website.
- The two most affected industry sectors are Retail (43%) and Financial (19%). These two also happen to be two of the most popular industries housed online. After all, who doesn’t shop or bank online these days? Therefore, it’s a clever move by phishers to target these industries and use them to deceive consumers.
How Do You Combat Phishing?
 Once phishing has completed its mission of stealing personal information, it can create utter chaos for those affected. And, for a business, this could include gaining access to sensitive areas of your network e.g. confidential client information such as financial records. This is bad news for any business, so remember the following:
Once phishing has completed its mission of stealing personal information, it can create utter chaos for those affected. And, for a business, this could include gaining access to sensitive areas of your network e.g. confidential client information such as financial records. This is bad news for any business, so remember the following:
- Just because an email features an official logo it doesn’t mean it’s an official email from that company, so don’t rely on this for authenticity.
- Safe websites will always begin https:// and not http://, so make sure you always check whether that all important “s” is present.
- Although phishing is best known for stealing bank information, phishers are likely to target anything from your personal email details to your Facebook login credentials.
- Credible companies will never ever request that you email personal information to them. If you receive emails demanding such information then just delete them as soon as possible.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More