Almost all cyber-attacks are due a common denominator: a mistake. We aren’t perfect, of course, but we can limit number of IT security mistakes we make.
Working on a PC is far from straightforward and, as a result, the sheer number of complex routines you must work through leaves plenty of room for mistakes. At the same time, all a hacker needs to take control of your system is a few milliseconds. Accordingly, even the smallest security mistake can leave your PC at the mercy of a hacker. However, by understanding what the most common, and usually simplest, IT security mistakes are, you can strengthen your IT defenses almost immediately.
Start Eliminating These Mistakes Today
If you want to make sure your IT infrastructure is safe from hackers, then you need to avoid these five IT security mistakes:
- Not locking your screen: you may trust your work colleagues, but the fact remains that numerous people will enter your organization’s premises throughout the day. Some may be familiar, some may not. And that’s why it’s crucial you lock your screen. All you have to do is hit the Windows button and the L key; your screen will be locked with a password and the contents of your PC immediately protected.
- Underestimating your value as a target: threat actors are malicious and, although they are certainly interested in big targets, they’re equally likely to target smaller organizations too. Additionally, many cyber-attacks are automated and don’t discriminate against who they attack. Therefore, never assume that your small business is of no concern to hackers. Remain vigilant and practice good IT security.
- Passwords on Post-it notes: we all know that remembering passwords is difficult, but the biggest mistake you can make is by writing your password on a Post-it note. And then sticking it to your monitor. Sure, it’s convenient for you, but it’s also highly convenient for anyone looking to compromise your PC. Instead, create passwords you can easily remember, but are difficult for anyone else to crack.
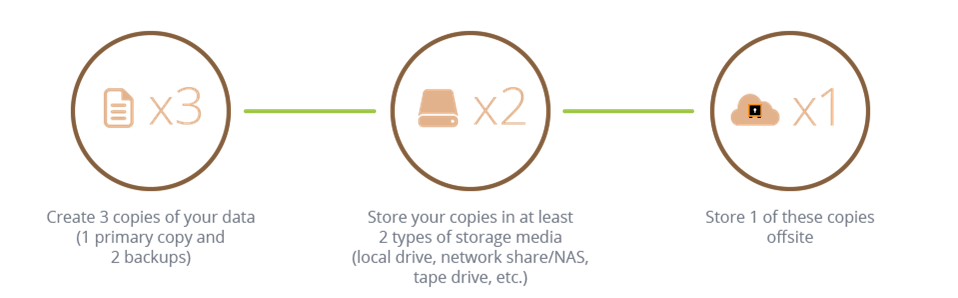
- Not backing up effectively: when it comes to IT, the range of backup options available in 2022 is plentiful. From on-site storage, to external cloud storage and even onto good old fashioned optical drives, there are numerous options. And it’s important that you use more than one backup option to protect your data, this will ensure it’s available when you need it. Remember: failing to maintain an effective backup process will seriously hurt your recovery time in the event of a cyber-attack.
- Assuming email attachments are safe: ever since email became a mainstay of modern communications, it has carried a huge risk of delivering malware through email attachments. Most concerning of all, these infected attachments may be sent by email contacts you consider safe, it could even be your colleague sitting next to you. Threat actors can easily take control of a victim’s email address book and email malware under the guise of the victim’s email address. And that’s why you should evaluate every email you receive.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More