Computers such as desktop PCs and smartphones have greatly enhanced our lives, but they also bring about many inconveniences. One of which is managing countless accounts that range from emails to a simple PC login screen. Most people have the capacities to remember a few important phone numbers and maybe a few more pins or passwords for various services. However, when it comes to all the services and accounts that a person must manage on a daily basis, it’s often hard to recall what the screen names and passwords of these accounts are right off the bat.
Rock, Paper, Software
Many computer users, despite the advantages that the computer age brought about, are still using stickies or notepads to store their digital usernames and passwords. While this method of management isn’t at all a bad idea, it does come with quite a few inconveniences. We can go on and on about what these are, but if you can just conjure up some common sense you’ll realize that a piece a paper isn’t going to cut it (pun intended) in this day age.
Rather than risking losing all their digital account information in the blink of an eye (i.e. misplacing your paper notepad), a lot people are now relying on software-based account organizers. These account managers, aka ‘password managers,’ have become quite popular, as they are easily accessible whenever and wherever.
KeePass: Rock Solid Password Manager Without the Fuss
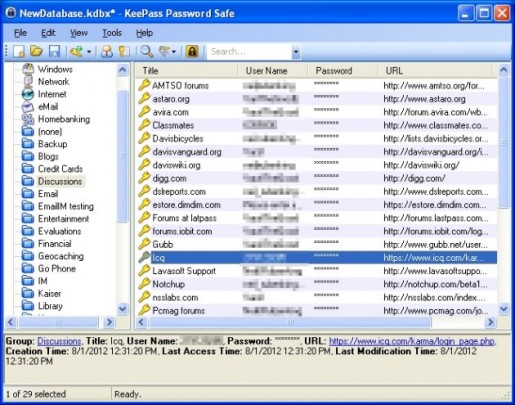
There are many password management options available, but nothing beats free—especially when it does the job. One such freeware (free software that is fully functional) is KeePass. This particular program isn’t flashy, but it is simple and extremely easy to use. It lets you store virtually all your digital account information in one place, and it even lets you synchronize this data with your Dropbox and Google Drive account. Just like a conventional paper notebook, you can record all your usernames and passwords into one place, and when you need to retrieve the data you can login into the program with a key file or just a password to obtain what you want.
Open Source and Free
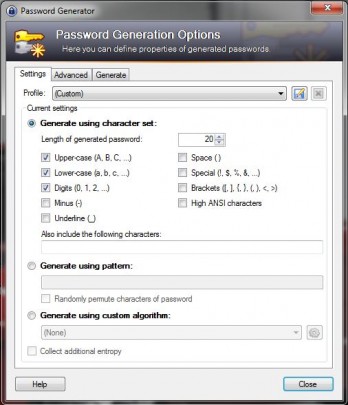
Another nifty built-in feature of KeePass is its password generator. One of the best ways to keep your personal information safe is to secure it with a password that’s difficult to guess, and KeePass’ password generator will help you do just that.
KeePass is also open source, which means programmers (or overly enthusiastic computer users) can examine the program’s code to see if it’s safe for use, and they can even modify some of the software’s settings to fit their needs.
Onsite PC Solution recommends KeePass to all clients because it gets the job done, and with little hassle. Did we mention it’s completely free?
For more tips on how you can better manage your digital accounts and cloud services, contact our IT professionals.
Read More