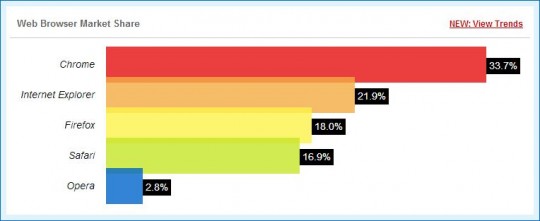
Browser share according to W3Counter
The debate about which internet browser is the best has essentially ended. Personal preferences aside, the consensus among most casual users as well as developers is that Chrome, the Google-backed browser, is number one (for the time being).
Why should you pick Chrome over all other browsers? First and foremost, let’s consider the fact that the browser is constantly being revamped and tweaked by a huge community of developers worldwide. Google gave developers the source code for Chrome back in 2008. Since then, the open source Chomium project has thrived, leading to a robust and constantly updated browser.
A Think Tank is Better Than One Einstein
What it comes down to is this, Google is allowing outside developers to tinker with Chrome. Among some of the crucial benefits resulting from the open collaboration of many brilliant minds are these:
- Exceptional security measures as developers are constantly debugging and patching up vulnerabilities
- Add-ons built around the Chrome browser allows for a highly customizable surfing experience. For instance, the adblock plugin lets surfers select which site is allowed to have ads or popups.
- Convenience. Users can sync their browsing history, usernames, passwords, and etc. across multiple platforms. By simply logging into one’s Google account, he/she can have access to all his past browsing history, and save his present browsing experience for future syncing on other platforms.
It Can Always Be Better
Google, with its involvement in adding parts to the Internet of Things (IoT), has greatly improved the browsing experience for most average internet surfers. Much of the work done in the development of Chrome (past, present, and future) ultimately serves as medium for Google to grow and profit. However, Google is taking input from outside developers, and thus it has given the search giant an edge in the browser war over its competitors like Microsoft’s Internet Explorer and Mozilla’s Firefox.
Although Chrome is an exceptional browser for almost everyone and every purpose, a tool for surfing the internet is only a piece of the personal computing experience. Chrome users will still need to consider what other tools will complement the browser, so that surfing the Internet becomes as secure as possible.
For more ideas and tips on staying safe and secure online, contact your office IT professionals.
Read More