Malware not only steals your personal data, but can also hijack your system and network resources to work on things you don’t approve of.
Bitcoin and other forms of cryptocurrencies have skyrocketed in popularity in recent months. The cryptocurrency craze isn’t reserved just for investors as virtually anyone can get their hands on these lucrative digital coins—given they have the necessary resources. What we’re talking about is: if you don’t have money to invest in Bitcoin, you can mine the Bitcoins. Mining these coins, however, will require some computer know-how and hardware.
Stealing Without Physically Taking
When it comes to knowledge of how hardware works and where digital information flows, cybercriminals and hackers are ahead of the game. What they lack is the hardware, but why do they need to purchase their own hardware when they can steal your processing power? All they have to do is run malicious code on your computer to hijack the computer’s resources remotely and us it to mine Bitcoins for themselves.
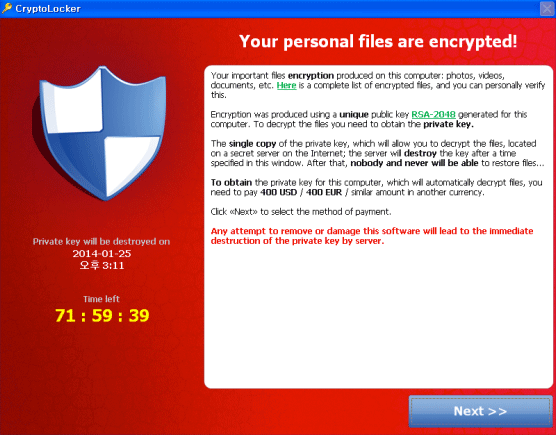
Beginning late last year, a slew of malware aimed at hijacking computers for mining Bitcoins began infecting unsuspecting victims. Where and how these tools make their way onto people’s computer can vary, but it is especially troubling if the source is a popular website like Yahoo.
Yahoo admitted in January that its advertising platform was utilized by cybercriminals to distribute hijacking malware and viruses. Fox IT, a cybersecurity firm, estimates that as many as 2 million Yahoo users were affected by the exploit. Yahoo, however, has not given an estimate how many of its users clicked the scam ads.
Must Click the Ad That’s Slick!
While most of us will try to ignore any type of ads that appear on a website, savvy marketers will always find a way to deploy attractive and mind boggling banners that will trick us into clicking. Criminals are also marketers in a sense, and so it is likely that they used these marketing tactics to lure people into clicking their ads on Yahoo.
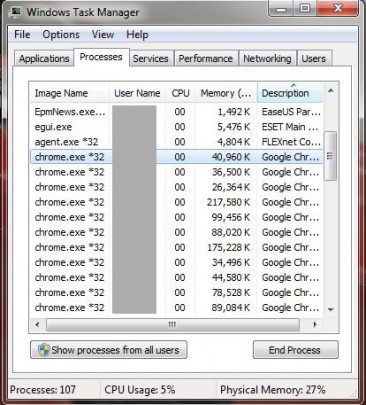
If you’re not running any resource intensive tasks, the task manager should display low CPU and memory usage.
If you’re a Yahoo user, and notice that your computer is running unusually slow as of late, check your computer’s resource monitor to see which process is taking up abnormally large amount of bandwidth, memory and CPU usage. Any process or application that is hogging up too much system resources could potentially be one of these Bitcoin mining malwares.
If you’re having a hard time navigating and figuring out whether or not you’re a victim of the Bitcoin malware, please contact our IT professionals and we’ll be more than happy to give you a hand!
Read More