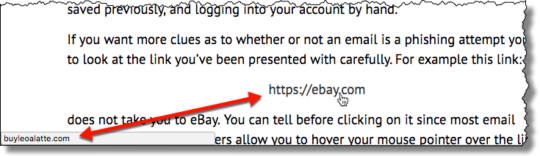
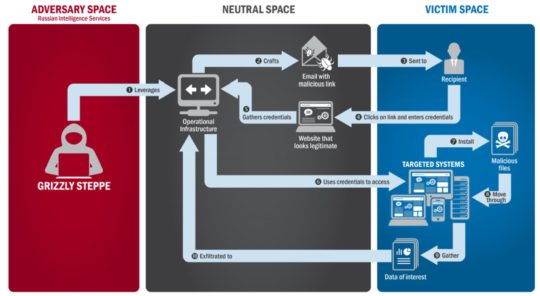
There’s no such thing as good malware, but some is certainly less trouble than others. And, when it comes to the Emotet malware, some are very dangerous.
First discovered in Europe in 2014, Emotet soon began to spread around the world and, before long, was infecting PCs in the US. Comprising several different functions and methods of attack, Emotet is a type of malware which has persisted in the digital landscape due to its constant evolution. Taking advantage of user errors and vulnerable systems, the hackers behind Emotet have managed to infect huge numbers of systems over the last four years. And it would appear that those who are coding Emotet are getting even cleverer.
Due to the severity of Emotet, and the lessons you can learn from it, I’m going to take you through the basics of Emotet.
What is Emotet?
Emotet is known as a banking Trojan due to the way it specializes in stealing user credentials including banking data as well as numerous other credentials. This is achieved by the injection of malicious code into infected computers which allows Emotet to transmit sensitive information.
As with numerous other brands of malware, Emotet delivers its payload through a combination of malicious URLs and infected attachments. Key to spreading the Emotet malware throughout a network is the way that Emotet takes advantage of the EternalBlue vulnerability, an exploit which affects unpatched versions of Windows XP through to Windows 7.
There is, however, more to Emotet than just stealing sensitive data. Adding another string to its bow, Emotet is also responsible for downloading other types of malware to infected PCs. These can include further banking Trojans such as TrickBot or modules as diverse as Outlook address book grabbers and spambots.
Why is Emotet So Clever?
The hackers behind Emotet are highly talented and this is why Emotet is so difficult to detect. Dedicated to their software, the hackers regularly update the code behind Emotet and this is then communicated to compromised systems. This change in Emotet’s DNA allows it, therefore, to remain undetected. Just as security experts believe they had identified the key signature of Emotet, they’re faced with a new variant which renders their work redundant.
New research has also revealed that Emotet’s Command and Control (C&C) server is split into two separate clusters. By designing their C&C server in this manner, the hackers can ensure that the source of Emotet is harder to track down. Additionally, this split of the C&C server allows Emotet to keep functioning if either of the clusters suffers a technical issue. For authorities, disabling this setup is highly difficult and underlines why Emotet has been so successful.
How Do You Protect Your PC from Emotet?
It’s important to protect your organization from malware at all times and variants such as Emotet are the perfect demonstration of why it’s crucial. So, if you want to maximize your defenses, make sure you follow these best practices:
- Run all updates and patches to provide security to your hardware and software
- Segment your network to ensure that malware cannot spread through your entire network
- Backup all your files to reduce the need for any downtime in the case of infection
- Educate you staff in order for them to know what they should and shouldn’t click
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More