Cryptowall can bring your business to a screeching halt. Here is how you can protect yourself against what’s becoming the most malicious malware of 2014.
You don’t need to end up in trouble. We’ve outlined some very important guidelines on what to do to avoid an attack like Cryptowall and Cryptodefense:
- Scan any email attachments that land on your email account– especially PDF attachments, which can be disguised as either payments, invoices, receipts, complaints and so forth. This is generally how this Trojan enters the system.
- Avoid clicking on any advertisements– not only does this attack happen through attachments, they have also been identified through infected banners on different web pages. Avoid clicking on them at all costs!
- Avoid mapping drives directly to servers– For any person with administrator rights, if you’re working from your computer, aim to use remote access tools as needed. This will help reduce risk to the servers directly.
- Lock down admin users– assign user accounts by name, so that if an attack happened, the user’s account can be frozen to avoid its credentials being for further used for unauthorized installations.
- Verify Backups– a backup is only good if it’s one that can be restored. Test your backups regularly.
- Off-site or offline backups– having these will reduce the chances of suffering from a single point of failure due to such an attack. Please note that mapping Dropbox on your computer can still make it subject to this attack.
- Whitelisting approved software– you can find tools and systems that can help you with these. You can specify what can run on any system on the network.
- Utilize Windows Group or Local Policy Editor – Software Restriction Policies can be created to stop executable files from running on any given path.
- Have a Bitcoin account set up in case nothing else works. Being prepared can help you save time.
Here’s what you can do if you find yourself compromised:
- Update your AV definition files and scan your system with it -It may not remove the Trojan, but it can remove other nasty programs that it may have allowed to run.
- Isolate– do this on the affected workstations and disable user accounts involved ( especially if it has admin rights), as mentioned previously.
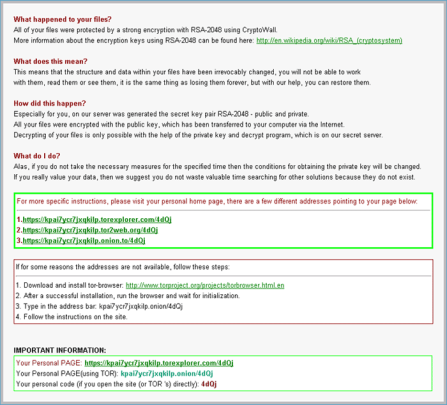
- As a last resort -if all else fails, you may need to pay the ransom. A support file is provided within the given website from the infection. It would indeed be a hard lesson learnt!
Like they say, prevention is better than a cure.
For more ways to protect yourself and your business from malicious attacks, contact your local IT professionals.
Read More