CryptoWall 3.0, a new variant of the Cryptolocker ransom-ware virus is out causing problems to many businesses. Learn how it works and how to prevent it.
CryptoWall 3.0, a new variant of the Cryptolocker ransom-ware virus is out causing problems to many businesses. Learn how it works and how to prevent it.
Discovered in late February 2015, CryptoWall 3.0 works very much like the previous versions of this virus, however its strategy to infect systems is somewhat different..
How CryptoWall 3.0 works
- When the infected file containing CryptoWall 3.0 is opened, the malicious program encrypts all files that it finds mapped over the network.
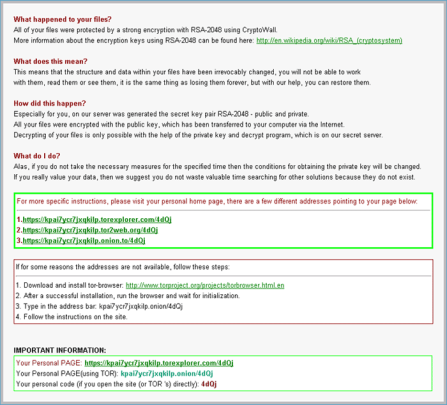
- Files become encrypted and unreadable.
- Only the perpetrator can unlock the code to make it readable again.
- Once it finishes encrypting all files, it asks for a ransom of around $500USD.
- This amount is expected to be paid in Bitcoin currency, which is a universal currency used around the world.
Point of entry and identification
CryptoWall 3.0 employs social engineering tactics via phishing emails. These come through with attachments disguised as an “incoming fax report” displaying the same domain as the one the user is on creating a false sense of trust by making them believe it is a legitimate document. Once opened, Cryptowall picks up all mapped drives identified from the host machine it infects and encrypts all of the contents on it as well as the data on the mapped drives.
CryptoWall 3.0 uses .chm attachments, which is a type of compressed file used for user manuals within software applications. Since .chm is an extension of HTML, this allows the files to be very interactive with different types of media such as images, hyperlinked table of contents and so forth. It also uses JavaScript to allow the attack to send users to any website on the Internet, which occurs when a user opens up the malicious .chm file.
Once the file is opened, the attack automatically runs its course.
CryptoWall: More than meets the eye
Ransom Malware bas been evolving since the first wave of Cryptolocker attacks back in September 2013, which had netted the virus writers over $27,000,000 from claiming ransom money within only a few months of the Cryptolocker operation. Attacks are happening all over the world with detections in Europe, the UK, the US and in Australia.
The sophisticated Cryptolocker and CryptoWall attacks also use botnets, which is a wide network of compromised machines, to be the originators of the attack. Aside from speeding up distribution of the virus, it allows anonymity for the virus writers.
How to prevent CryptoWall 3.0
- Set up a rule in your email filters to black list .chm file extensions.
- Stay on top of your backups with daily backups which are verified and tested- also have an offline copy of your backups.
- Update your office applications baseline such as Java, Adobe Flash player etc…
- Patch any vulnerabilities on Windows systems, especially on all Servers.
- Be sure to have the latest Anti-Malware signatures.
For more ways to stay protected and safeguard your network, contact your local IT professionals.
Read More