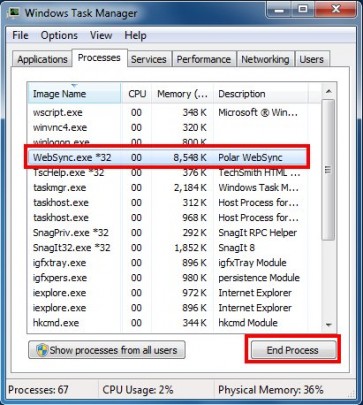
Can you list all of your licenses? From audits to system failures, tracking software licenses is a crucial part of keeping your business flowing smoothly.
We know how tedious this can be. Managing software is a little more complex than counting the number of physical assets, such as computer desktops and monitors.
Why would your business track software licenses?
We’ll use the BBC as a brief case study. They have over 27,000 computers on their network across the UK. As you can imagine, they’ve encountered a huge problem in the past when they needed to run an audit for all of the installed software on their endpoints. They were lost as to what was really being used on all staff computers. For example, a particular software package was purchased for 3,000 desktops; however, they eventually came to realize that only 300 were actually being used!
They found both legal and out of compliance software packages. They eventually decided to run a weekly audit to keep all of this under control. Prior to this, both hardware and software assets were de-centrally managed by each of their own departments, with no common procedure.
Big impact for small businesses
Users can have all sorts of software installed on their computers which can vary from Microsoft Office, Windows, Quickbooks and so forth. So think about this for a moment. What if your computer crashed today or worse yet, what if an employee reports their laptop stolen or completely kaput, what do you do about it?
You will likely search your storage or server room in desperation to find your previously purchased software. But wait, where’s the license? Nowadays, most software is available virtually over the cloud. Paper licenses and CDs have been replaced by electronic virtual software!
In the event of a computer crashing, there is of course a list of other important considerations regarding why a business needs to keep track of their software licenses.
- Productivity. If not monitored systematically, it wastes time, resources, making it unproductive for both the business and staff. For instance, staff may need to spend an additional few hours to track software manually. Even then, the tracking may not be 100% accurate!
- Less surprises. Your business and users can keep in compliance with EULAs, helping you to avoid expired software usage, which would also be outside of software support. In addition to this, it would prevent any disruption made to business operations as they would have fully functional software packages.
- Understanding the software usage of your company. You can be in control and manage software usage, as well as making better purchasing decisions in regards to the exact amount needed over a given period of time.
- Meeting budgets. Continuing from the last discussion point and using the BBC example, once you understand the realistic demand for a particular software package, you can save a significant amount and reduce costs from purchasing 3 licenses as opposed to 30.
- Free up unused licensed keys. Every business knows the daunting task of having to re-purposing equipment or taking some out of service. With this taken into account, it is also important to consider what software may be installed that could be using up licenses or may be making the license key dormant.
Solutions
One piece of software that allows you to track thousands of software licenses on your office computers is called Recover Keys. Recover Keys allows you to find licenses to your computer Operating System, Office Products and 6500+ other pieces of software installed throughout your systems.
Aside from digging up licenses, Recover Keys has the following features:
- Backup activation keys
- Scan another Windows system or HDD
- Scan remote network computers
- Automatic updates
Onsite PC Solution offers software license tracking and management as a part of our managed service plans for your business. For more information on tracking license and maintaining good IT policy in your office, contact your local IT professionals.
Read More