Virtualization is gaining popularity in many businesses. What is virtualization and will the benefits help you streamline and protect your business?
The idea of a machine not being physical may sound like a bizarre idea. Here is an easy breakdown of virtualization:
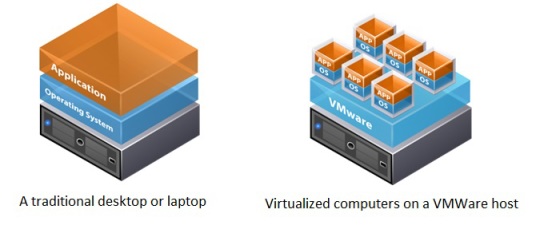
- In simple terms, virtualization is a virtual representation of something that can be physical like a desktop, server, storage device or another physical resource.
- Just like your desktop or laptop computer, a virtual machine will perform and behave just like a real physical one.
- When a computer is virtualized, it is no longer running on hardware like your desktop or laptop computer. Instead many computers can run on one system.
- For virtualization to be possible, there needs to exist a physical machine, which is known as a host.
- A host will hold a virtualized guest machine. For example, you can have a Windows computer that can host a virtual machine running Linux on it. Both systems can co-exist within the same machine running completely separate from each other.
- The software or firmware used to manage the virtual machine is known as Virtual machine Manager or a hypervisor.
Virtualization can be classified into three categories.
- Full virtualization. Nearly all of hardware is simulated. It runs complete with its own guest OS, and it runs unchanged.
- Partial virtualization. Only a portion of the environment is virtualized and a little configuration needs to be applied to some of the guest programs in order for them to run.
- Paravirtualization. In this setup, only the guest programs are virtual and run within their own boundaries, as if running on a completely different system. The programs run by the “guest” need configuring in order to run in such an environment.
Where it all started
It first existed during the 60s on, what was known as, mainframes, which were huge heavy duty machines, much like servers. These mainframes used virtualization to split up the machines resources to run various applications. From then on, virtualization has evolved to what it has become today. Whole operating systems with applications can be virtualized allowing individual users to interact with an entire system for themselves.
Benefits of virtualization
Now that we have a better understanding about the whole virtualization concept, we can briefly look at some of the main benefits to virtualizing a system.
Space saving– Think about how much space you’ll save in a computer equipment room by having one single machine running multiple virtual machines. For instance. these can run servers to fulfill an entire business. An example of a hardware reducing ratio, by VMWare, is 10:1. All this will considerably change your server architecture.
Maximizing server efficiency– Within each virtual server in the host, you can seamlessly run multiple applications as well as different operating systems.
Reduces costs– By having less physical machines to purchase and maintain, you save a considerable amount of electricity, whilst helping to maximize productivity on servers and allowing business operations to run smoothly.
Easy to mange applications and resources– Migrations can happen whilst on a live environment, servers can be cloned at the click of a button, easy to set up load balancing over virtual farm servers and it’s easy to scale.
Final Thoughts
There exists a handful of leading virtualization vendors who offer different solutions according to your business and infrastructure needs. Some of the big names include VMware, Citrix, Microsoft Hyper-V and the like.
Do you use a Virtualization platform? If so, let us know what you think and how you rate it.
To determine whether virtualization can help streamline your business’ productivity, contact your local IT professionals.
Read More