Most public spaces from coffee shops through to shopping malls now contain some form of public WiFi, but are these public networks 100% safe to use?
When your office based employees connect to the internet, they’re making this connection through your own network. And this means that you’re able to monitor all incoming and outgoing activity. Rather that monitoring which websites your employees are visiting, though, the main reason for monitoring these connections is to make sure that nothing malicious is entering your network. Remote workers, however, are likely to take advantage of public WiFi as a considerable amount of their work will be completed away from your work connection.
Due to the unique nature of each and every public WiFi network, it’s crucial that you understand the concerns surrounding these types of connections.
The Dangers of Public WiFi
Public WiFi may appear to be extremely convenient, but there are a number of security issues attached to connecting to public hotspots such as:
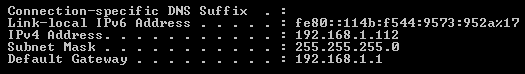
- Lack of Details: When you connect to a public WiFi network there’s no way of knowing exactly what you’re connecting to. This, in itself, is a dangerous move and is one of the main reasons why public WiFi is frowned upon by security experts.
- WPA2 Vulnerability: Most public WiFi uses WPA2 encryption to protect data, but the security of WPA2 has been called into question over the last few years due to the discovery of a major vulnerability in its code.
- Malware Threat: Due to the lack of security surrounding public WiFi networks, it’s very easy for a hacker to position themselves in between the connection point and, for example, your laptop. This allows the hacker the opportunity to discreetly upload malware to your device and execute its malicious payload.
Should You Use Public WiFi?
Clearly, there are a number of risks involved in using public WiFi and the simplest way to avoid these dangers is by completely avoiding these connections. However, there are certain scenarios where it’s crucial that your remote employee needs to connect to whichever network is available. And in these cases you should follow these best practices:
- Use a VPN: A virtual private network (VPN) is a service that creates an encrypted connection between your device and the remote server of your VPN. Any hacker who manages to intercept this connection will only be able to view a highly encrypted message which will be absolutely useless to them.
- Verify the Connection: One of the simplest ways to evaluate the connection on offer is to double check the legitimacy of the available connections with an employee at the location in question. At the very least they will be able to confirm whether the connection is genuine or fake.
- Use Anti-Malware Software: Protecting yourself with anti-malware software should be a given, but when people are using remote devices they fail to appreciate just how vulnerable these are. Even the simplest form of anti-malware software provides an effective defense, so make sure your device is protected.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More