Many of us will have started preparing our tax returns and hackers are well aware of this. Therefore, it pays to be aware of the numerous online tax scams.
Nobody likes completing tax returns due to the vast amount of data involved. However, they’re essential for organizations to remain operating. And that’s why we spend hours and hours collecting receipts and details for transactions; this is where all the data builds up. Hackers, of course, like nothing more than getting their hands on huge amounts of data. This data can be used for both financial gain and damaging an organization. Accordingly, tax season is their hunting season.
Tax Scams to Look Out For
Countless tax scams are currently circulating in the digital wild, but these are the most common ones you will encounter:
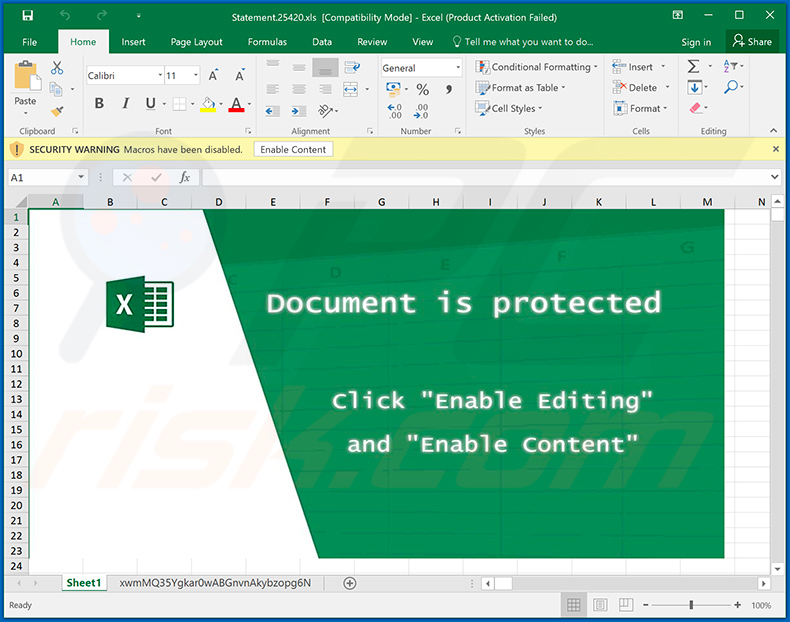
- Automatic Tax Payment Deduction: A number of emails have been discovered which claim to originate from the Income Tax Department. These emails falsely claim, in order to generate anxiety, that a tax payment has automatically been deducted from their bank account. An attachment is included which masquerades as a receipt for this transaction. Hackers hope that the recipient’s anxiety and confusion will cause them to open this receipt. Unfortunately, contained within this ‘receipt’ is a slice of malware named W32.Golroted.
- Fake Government Websites: A popular method for scamming victims out of money is by designing Government websites which look authentic, but are fake. Using information which has usually been stolen through malicious files or social engineering, these fake websites inform victims that they have received a tax fine. The only way to pay this fine is by wiring payment or purchasing general purchase reloadable cards. However, there is no fine to pay and all the victim will be doing is bankrolling the hackers.
- IRS Tax Return is Locked: The last few years have seen the emergence of a phishing email which claims that access to the recipient’s tax return has been restricted. The email is designed to look as though it has been sent by the IRS or, sometimes, the manufactures of the popular TurboTax software. The truth is that the email is fake and has been sent by hackers. The email will urge recipients to click on a link which will take them to a malicious website where their personal information will be stolen.
Staying Safe During the Tax Season
Despite the number of online tax scams it’s easy to stay safe during the tax season. All you have to do is follow these best practices:
- Remember that the IRS will never contact you by email to discuss the nature of your tax return or your personal details.
- Verify the true identity of any suspicious links by hovering your mouse cursor over the link. A popup will then display where the link will send you.
- Never send personal documents to unsolicited email requests as it is likely that a hacker is trying to harvest your details
- Emails that claim to be from official organizations, but do not use your name are to be treated as highly suspicious and should be deleted.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More