Hackers are keeping busier than ever and evolving their strategies almost daily; their latest method for attack is to target the humble resume.
Ask any HR professional to tell you how many resumes they receive in a week and they will be able to show you a mountain of them. Even in a business landscape which has changed dramatically over the last 20 years, a resume remains a crucial calling card for employment. And this is why hackers are keen to exploit them. It’s not just that a resume can easily be loaded with malware, it’s more that organizations are so familiar with them they are unlikely to suspect them.
Hackers, of course, thrive on complacency, so it’s time to take a look at what could be lurking inside that next resume.
Malware Laced Resumes
Resume themed scams are on the rise in the US and this latest installment centers around the use of the ZLoader malware. As with many strains of malware, ZLoader is designed to steal credentials. These credentials can include stored passwords and browsing histories, but also banking credentials. And what’s most concerning is that many of these infected resumes are being sent to financial institutions.
But what exactly do these compromised resumes look like? And how are they activated? Well, this is what happens:
- Recipient receives an email with a title along the lines of “Job Application” or “Advertised Job”.
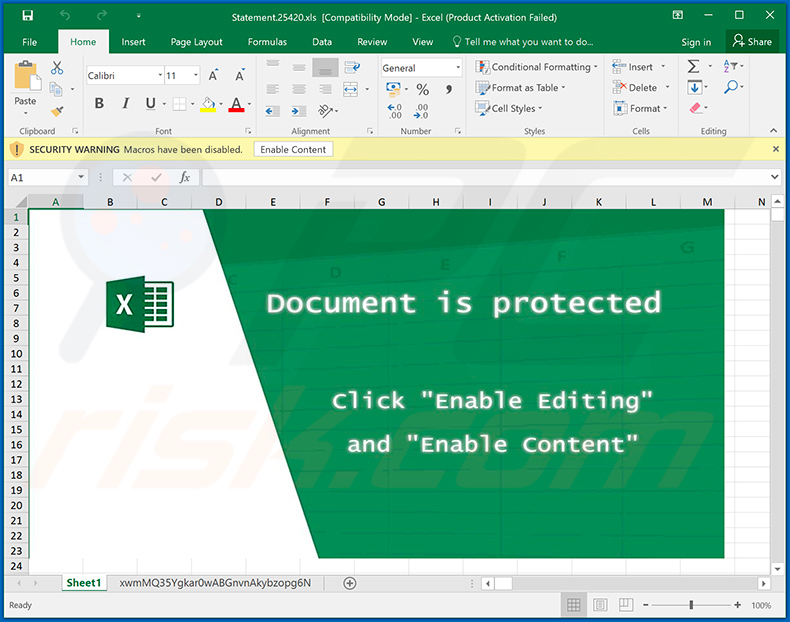
- Upon opening the email, the recipient is encouraged to open an attached Excel document which claims to be a resume.
- If the Excel document is opened, the recipient is then prompted to activate a macro to enable the content.
- Unfortunately, activating the macro will only enable a download of the ZLoader malware to the recipient’s PC.
- One of ZLoader’s main attack strategies is to infect systems with a malicious app called Zeus which can record keystrokes and steal banking information.
How to Tackle Suspicious Resumes
ZLoader is a form of malware which has been around for several years now. And, thankfully, this means that many anti-malware tools are effective at identifying it and eliminating it. However, if ZLoader is only active for a few minutes it can steal valuable and damaging information. Therefore, it’s always advisable to practice the following:
- Be Wary of Attachments: Even the most trusted source can be compromised and at the mercy of digital attacks. Say, for example, you receive a resume from a friend – does this mean you should open it without a second thought? The answer is no and this is because your friend’s email address could easily have been hacked. All email attachments should, as a result, be scanned with anti-virus software or checked by an IT professional.
- Never Enable Macros: A macro can be very useful for automating certain processes and features in an Office document. But this also makes them perfect for launching malware attacks. If you are ever prompted to enable a macro within an Office document you should verify that it is safe to run. And, again, this should be verified by an IT professional who will have more experience with malicious macros.
For more ways to secure and optimize your business technology, contact your local IT professionals.