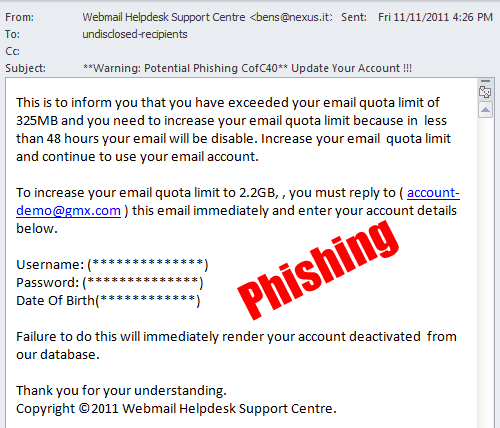
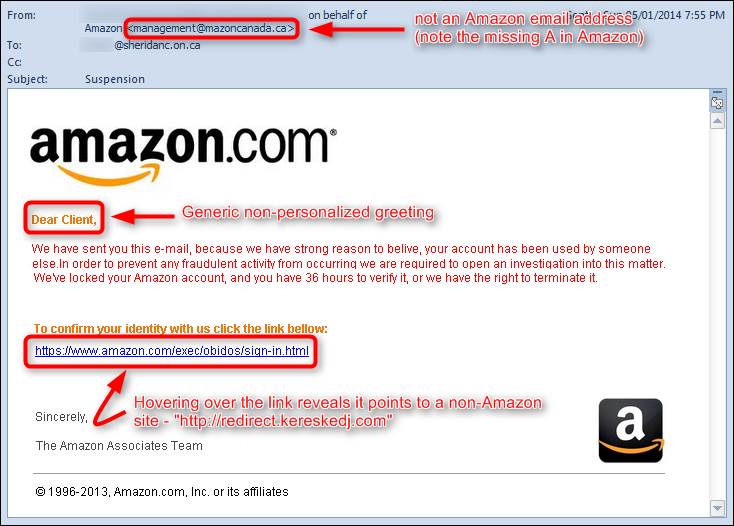
Phishing is now so prevalent and sophisticated that even the biggest organizations on the planet are likely to be duped by phishing scams.
Immunity from such attacks is a difficult privilege to secure, so any organization that wants to remain productive needs to understand the threats out there. While you would expect most phishing attacks to target smaller, less secure organizations, this couldn’t be further from the truth. Instead, many hackers are taking on high profile organizations due to the challenge on offer and the publicity that such attacks bring.
Understanding how these businesses have been phished is crucial as it helps you to understand exactly why you need good security. To provide you with a foundation of knowledge, we’re going to look at some high profile organizations that have been phished.
Facebook and Google
Two of the biggest names in business on the planet, Facebook and Google found themselves at the center of the same phishing scam a couple of years ago.
Evaldas Rimasauskas, from Lithuania, used a simple phishing campaign whereby he posed as the head of a Taiwanese parts manufacturer called Quanta. Key to this scam was that Facebook and Google both used the genuine Quanta company to conduct business with. Through a combination of compromised emails, forged invoices and a lack of suspicion on the two tech giants’ behalf, around $100 million was paid out to Rimasauskas between 2013 – 2015.
Anthem
Anthem is one of the largest health insurance companies in the US and, as you can imagine, they hold a substantial amount of private and confidential data. However, in 2014 they lost nearly 78.8 million consumer records due to a phishing attack.
It’s believed that a foreign government was behind the attack, but the method employed was still ridiculously straightforward. An employee at an Anthem subsidiary opened a phishing email which allowed malicious content to be downloaded to the employee’s PC. Once these files were executed, hackers were able to take control of the PC by remote access and start making their way deep into the Anthem network. One of the sections that were of most interest was Anthem’s data warehouse where the hackers had access to customers’ medical histories, social security numbers and address details.
Snapchat
The popular social media app Snapchat found one of its employees being targeted by a spear phishing scam in 2016 which compromised confidential data.
A seemingly innocuous email was sent to Snapchat’s payroll department in February 2016 which claimed to have been written by the company’s CEO. The email requested that employee payroll information was forwarded on for internal reference. Unfortunately, one of the payroll employees did not realize this was a less than genuine request. A significant amount of personal information about former and current employees was then emailed to an external party. Due to the nature of the data obtained, hackers then had the potential to use it to engineer identity theft.
RSA Security
Even IT security companies aren’t safe from the threat of phishing emails as RSA security discovered back in 2011.
Hackers designed two separate emails which were sent to four employees at RSA’s parent company EMC. The emails, which appeared to be from a recruitment website, contained an attachment referred to as ‘2011 Recruitment plan.xls” in the email’s subject line. However, this was a malicious attachment and, upon clicking it, a zero-day vulnerability in Adobe Flash would be exploited and lead to the download of a backdoor virus onto the user’s PC. The hackers were then able to access RSA’s network where they had access to 44 million employee records.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More