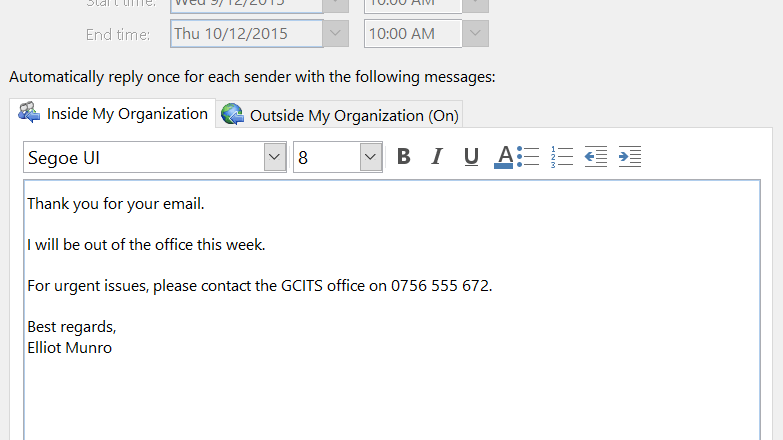
We’ve all seen a pop up on a website which asks you to accept cookies. And we tend to click yes. But do we know what we’re agreeing to?
Cookies have been part of the internet since the dawn of the world wide web, but most internet users are unclear on what they are. Yet, concerns have been building about them for several years now. 2011 saw the European Union (EU) passing the Cookie Law which states that websites need to seek consent before exposing you to cookies. Most popular websites attract users from the EU, so even US based websites, in theory, need to seek this consent.
The Cookie Law has heightened concerns around cookies, so it’s time to brush up on exactly what a cookie is and how it can affect your security.
What is a Cookie?
The simplest explanation of a cookie is that it’s a piece of code used to track your online activity. Naturally, this sounds sinister and contributes towards the concern over cookies. But most cookies have harmless motives. Their main objective is to remember useful information about specific users e.g. login details to keep you logged into websites and credit card details to autocomplete online forms. These ‘authentication’ cookies are useful allies for online life. But ‘tracking’ cookies receive considerable cynicism.
A tracking cookie records and broadcasts your web history, a rough location of where you are and the device you’re using. These are all pieces of data which help to identify personal information. And no internet user wants to reveal this to anonymous strangers. But these details can be shared by third-party software such as Google Analytics. This is why we live in age where personalized online ads crop up with an alarming regularity.
Keeping Safe with Cookies
Cookies carry a security risk, but as with most online activities it’s possible to negate and reduce these risks. To protect yourself for the more dangerous aspects of cookies make sure you do the following:
- Always be careful when sharing personal information. Cookies can transmit this information, so tread carefully. And if you’re using a public computer then do not send any personal information.
- Disable the storage of cookies in your internet browser. This reduces the amount of information being shared and can be adjusted in your browser’s privacy settings.
- Browser add-ons are available that block third-party software such as cookie trackers and ensure that your browsing habits remain private.
- Always make sure you have anti-malware software installed on your PC as malware can often disguise itself as harmless cookies or infiltrate advertising networks.
- If a website asks you to accept cookies and you’re unsure of its legitimacy then leave the website immediately.
Final Thoughts
There have been calls for cookies to be banned, but this is unlikely to happen any time soon. There will always be some form of online tracking in our internet experience, especially while it is being pushed by Google, but you can still remain safe by being vigilant and clever.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More