You have may have heard the Internet of Things (IoT) mentioned several times in the media and by colleagues, but what exactly is it?
Thankfully, the good news is that the IoT is a relatively simple concept and, more importantly, it can make a huge difference to your organization’s IT operations. It’s likely that you’re rapidly becoming interested in the IoT the more you hear about it, so wouldn’t it be amazing if you had a quick guide to the ins and outs of the IoT? Well, you’re in luck as that’s exactly what we’ve put together for you.
What is the Internet of Things?
Any business, no matter the size of its operations, needs to use a wide variety of IT devices on a daily basis. Traditionally, the majority of these devices have been connected by cables and controlled directly by the end user or through an onsite IT team with access to the network. The IoT, however, brings a whole new level of accessibility with its revolutionary use of internet connections.
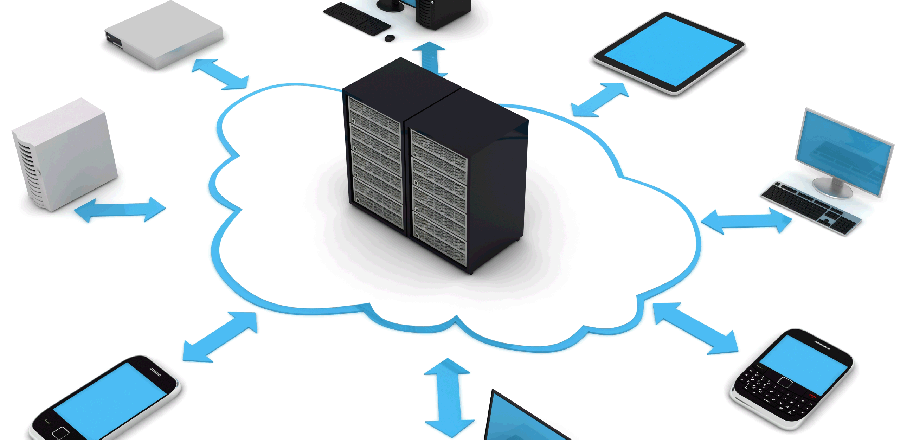
Put simply, the IoT allows users to connect devices to other devices and networks that can accept an internet connection. Sure, it may sound as though this is merely using wireless capabilities and nothing new, but the IoT is significantly different. Connecting to central servers through an internet connection means that your organization’s networks and smart devices can be remotely controlled from any location in the world.
What Can You Do with the Internet of Things?
The accessibility on offer from the IoT is clearly an interesting proposition, but what exactly can your organization use it for? To be honest, it’s a more a case of what you can’t use it for. Let’s take a look at some of the IoT most popular uses:
- Remote Working: As long as your employees have an internet connection, they can connect to your organization’s networks and access email, databases and files just as easily as if they were sat in the office at their workstation. This is highly beneficial for employees who are working away on business, but it also opens up a whole new world of remote working which, with studies showing it’s highly beneficial for staff, could seriously increase productivity.
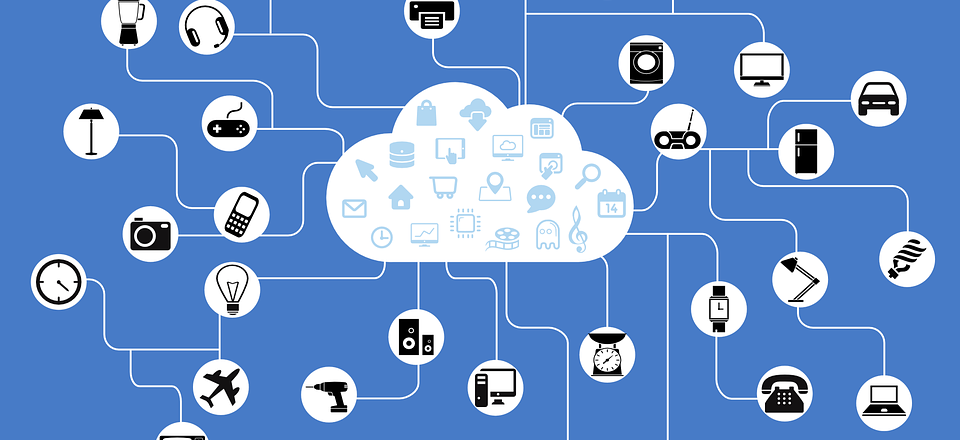
- Collecting and Sharing Data: The amount of data in use by businesses is getting bigger and bigger, but monitoring this is becoming more difficult with traditional IT setups. However, IoT devices are so varied and widespread that it’s now possible to collect data on almost any element of business you want. Tracking vehicle data, for example, through the use of IoT trackers can allow you to make use of your vehicles more efficiently.
- Enhance the Customer’s Experience: The lifeblood of any organization is the customer base and thanks to the IoT you can understand their needs better than ever before. IoT sensors installed in products such as, for example, refrigeration units can remotely monitory temperature fluctuations and, if necessary, send alerts when temperature thresholds are breached.
The IoT Is Here to Stay.
With over 26 billion IoT devices due to be in use by the end of 2019, the IoT is clearly making a massive impact on the IT landscape. With a number of benefits that can make a significant difference to the way your organization works, it’s time to start embracing the power of the IoT.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More