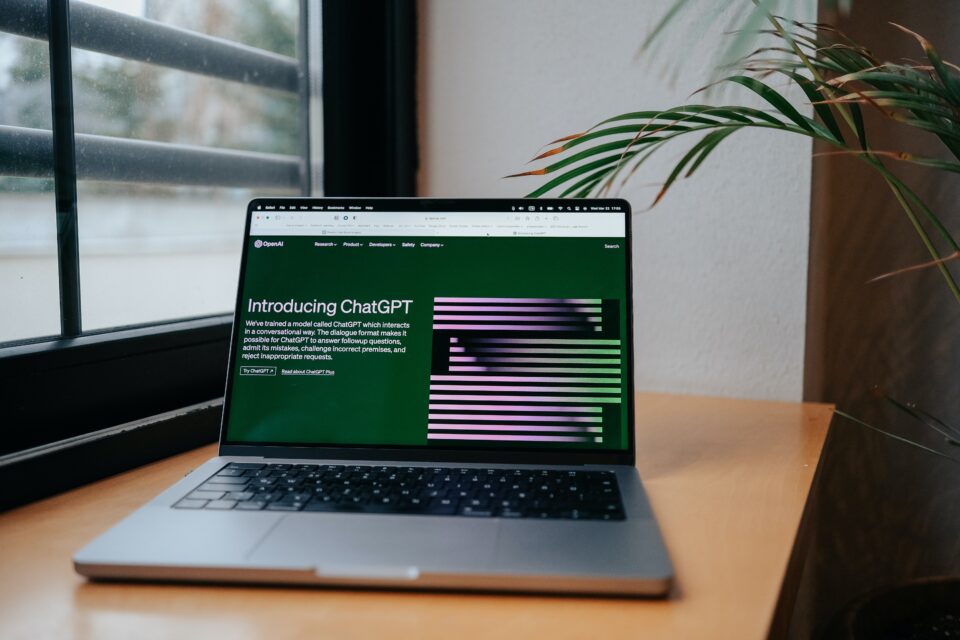
The launch of ChatGPT and its accompanying headlines have been heard around the world. And threat actors are leveraging this interest to launch new attacks.
You don’t have to look hard to find a headline relating to ChatGPT, the latest and most intriguing AI service to be released to the public. Everyone has been talking about it and, of course, this also includes hackers. After all, anything which proves popular – such as social media and cryptocurrency – quickly becomes an attractive method of delivering malware. Now, while you and your business may not use ChatGPT daily, this latest campaign utilizes a few attack strategies you need to be aware of.
How Has ChatGPT Got Caught Up in Malware?
The massive interest generated by ChatGPT means that AI related apps are at the forefront of most internet users’ thoughts. As a result, threat actors have decided to turn this interest to their benefit with their most favored technique: deception. The attacks, which were discovered by Meta, the owners of Facebook, have involved 10 different malware families and, on Meta’s platforms alone, 1,000 malicious links relating to ChatGPT.
Two of the most notable strains detected, which appear to have originated from Vietnam hacking groups, are NodeStealer and DuckTail. NodeStealer is a JavaScript-based piece of malware which is used to steal cookies and login credentials. DuckTail, meanwhile, not only steals cookies, but also focuses on hijacking Facebook business accounts to access lucrative ad accounts. Both of these malware strains are typically spread and activated via infected files or links to malicious websites.
How Do You Stay Ahead of AI Malware?
The official and genuine ChatGPT site has already been used by threat actors to develop new malware, so there is already concern about how it can be compromised. And this latest attack, while not directly involving the app, certainly adds fuel to the fire. Deception, of course, is nothing new in the world of hacking. But the number of people who fall for the duplicitous schemes of hackers is astronomical. Therefore, you need to remain on your guard by following these best practices:
- Educate yourself: Phishing scams and techniques are constantly evolving, so it’s important to understand the key basics of these attacks. Emails, for example, which include urgent or threatening language, requests for personal information, and suspicious URLs should never be trusted. Regularly educating yourself on these scams can help you avoid falling victim to malicious links and keep your online accounts secure.
- Only download from safe sources: downloading files from unknown sources can put your PC at risk of malware, viruses, and other types of cyberattacks. Accordingly, only download files from reputable websites and avoid clicking on links from unknown sources. Also, emails which contain attachments, especially those from unknown senders, should immediately be quarantined. These precautions will help protect your PC and your organization’s wider IT infrastructure.
- Use two-factor authentication: many of the malware strains identified in the latest round of ChatGPT-related attacks involve stealing credentials. Therefore, there’s never been a better time to implement a further layer of security in the form of two-factor authentication. While it won’t necessarily protect against session hijacks, two-factor authentication will significantly reduce the risk of unauthorized access to your accounts.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More