If you’ve worked away from the office then it’s likely you’ve set an out-of-office auto-reply on your emails. However, this could be very dangerous.
The problem with most out-of-office auto-replies is that they’re usually teeming with sensitive data. And this is data that anyone can harvest simply by sending you an email. There’s no filter on who receives the auto-reply. It’s sent to everyone. And this opens you up to a whole world of danger.
Let’s take a closer look at what these dangers are and how you can avoid them.
The Dangers of Auto-Reply Emails
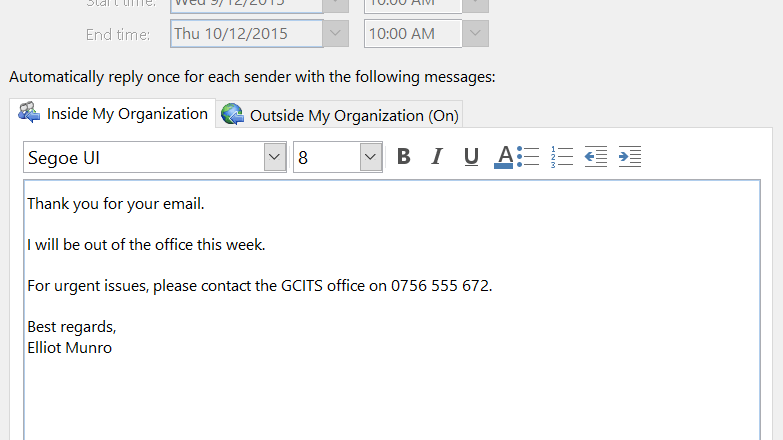
The type of out-of-office auto-reply email you’re likely to have sent in the past looks like this:
I will be out of the office during the week of October 21 – 27 at the Networking Conference in Houston, Texas. During this time please contact my assistant Ralph Smith on 555-2820 with any service-related issues. If you need to reach me directly then please call me on my cell at 555-1234 and leave a message
Peter Jones – Service Manager – Plant Manufacturing – Jones.Peter@plantmanf.com
This is an informative auto-reply and one that will help anyone that has a genuine interest in working with your business. But it also provides far too much information. It could compromise your safety and also the security of your organization. Social engineering is a criminal’s best friend and, in the above example, you have provided them with several pieces of valuable information:
- Availability: It’s not recommended that you reveal where you are and how long you will be there for in an auto-reply. In the example above it advises that Peter will be away from the office and his home for a set amount of time. Criminals, therefore, could plan to rob his home or, even more audaciously, turn up at his office and try to gain access.
- Signature: When you’re actively communicating with someone else in business it’s recommended to use a signature block at the end of your emails. This helps to underline who you are in the organization and the various ways you can be contacted. It’s an excellent communication tool, but only when it’s used wisely. You don’t want this information being sent to just anyone, so it’s best to remove this from your out-of-office auto-reply.
- Live Email Address: When it comes to email-spam there’s nothing the spammers love more than a confirmation that their spam has landed. And, when you set up an auto-reply, this confirms to any spammer that your email address is live. This information is then logged, automatically by spam bots, and your email address added to further spam lists as a worthy target.
- Chain of Command: It’s important to limit the organizational details in your out-of-office auto reply message, so revealing that, for example, Peter’s assistant is Ralph Smith is not a wise move. This not only helps to leak a further individual’s contact details, but it reveals an insight into the chain of command that’s in place. And this could allow a criminal to impersonate Ralph Smith to gain further access to your data.
Final Thoughts
The key to a safer out-of-office auto-reply is to provide minimal specifics when it comes to your excursion. You shouldn’t provide contact details and it’s safer to simply state that you’re unavailable when it comes to your location. By reducing the amount of sensitive data in your auto-reply you should be able to thwart any criminals and any security risks.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More