Chaos reigned supreme at Orly airport, Paris recently thanks to a technical fault on an old server running the ancient operating system Windows 3.1.
Yes, you read that correctly, the server was running on Windows 3.1 which is an operating system (OS) launched in 1992 and, as far as we thought, made redundant 20 years ago by Windows 95! It was the ancient nature of this OS which caused so many problems.
Let’s take a look at exactly what happened and the lessons it can teach us on maintaining and upgrading your servers.
All Flights Cancelled
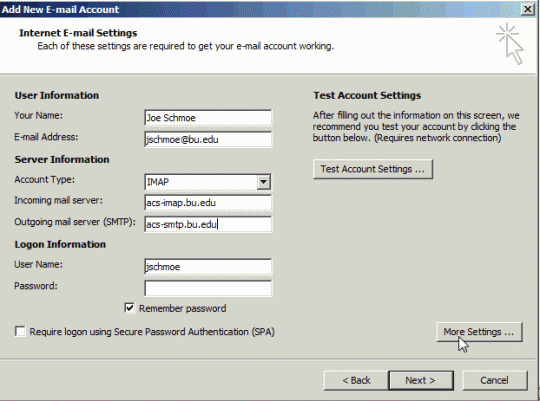
Pilots and air traffic controllers at Orly airport rely on a computer system called DECOR which helps communicate information about poor weather conditions. As you can imagine, this is crucial for taking off and landing, so it’s a vital piece of software. However, the problem is that DECOR doesn’t run on the lovely new OS Windows 10. Neither does it run on Windows 7. Or even Windows XP.
Instead, it uses the antiquated OS Windows 3.1 which certainly seemed a marvel back in the early 90s, but these days it looks like a dusty relic from the past. And, due to a glitch in DECOR, air traffic controllers were suddenly unable to relay critical runway conditions to their pilots. As a result, all flights were grounded as technicians raced to find a solution.
Outdated Software on Old Server
For an airport, having all your flights grounded is an absolute disaster, but Orly airport only has themselves to blame.
Upgrading your software intermittently is very important for the health and security of your servers. By ignoring this practice you run the risk of the following:
- Loss of knowledge: Alexandre Fiacre – from France’s UNSA-IESSA air traffic controller union – has conceded that they only have three specialists who understand DECOR. One of these is retiring soon and they still haven’t found a replacement. Due to the obsolete nature of Windows 3.1 it’s unlikely any newcomers will have the required knowledge either.
- Lack of Spares: Outdated servers, naturally, use outdated parts. And this becomes a huge issue when a spare part is required. Many manufacturers these days don’t like to give more than a 10 year lifespan for products, so parts are often made obsolete after this cut off point. And if the parts are no longer available for your server you’re going to face a big problem when they fail.
- Risk of Hacking: The lack of interest in an old piece of software such as DECOR means that the creation of any security upgrades and patches would have ceased a long time ago. This opens up the software to potential hacking incidents where the client will be left defenseless.
How to Avoid An Orly Airport Incident At Your Business
The simplest way to ensure your servers can be maintained efficiently is to upgrade them every couple of years. Sure, this has financial ramifications, but is less disruptive and embarrassing than having to temporarily close your business.
France’s transport minister has promised to upgrade the Orly’s software by 2017, but in our opinion that’s too late. It should have been upgraded in 1997!
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More