A number of Linksys and Netgear DSL modems have been found to be exploitable via a simple hole in the components’ firmware.
How Was This Discovered?
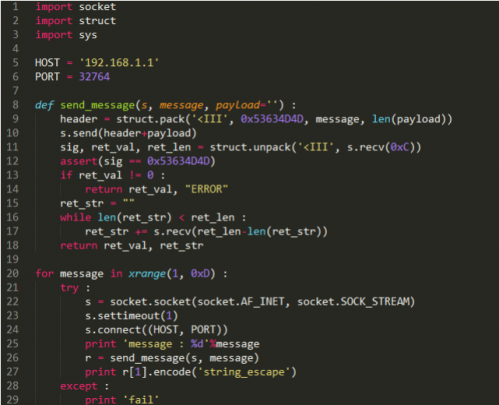
Eloi Vanderbeken recently took up the task of reverse engineering his Linksys WAG200G wireless DSL gateway’s firmware. At first he did it just for kicks, but during the process he found out even brand name tech components are just as vulnerable to hackers as off-brand products. Vanderbeken found out during his self-imposed hack-a-thon that his WAG200G DSL gateway was accessible to hackers via an undocumented port.
After Vanderbeken toyed around with the Linksys firmware, he was able to come up with a simple interface that allowed him to send various commands to the gateway without administration authentication. At first, Vanderbeken found that he couldn’t do much with the interface besides resetting the gateway to its factory settings. However, as he delved deeper into it, he found that he could inject some home-brewed command lines into the interface. These simple code injections allowed him to gain control of certain administrative properties using a wireless connection, and to reset the gateway’s web password.
How To Check if Your Are Affected
People interested in the hack and are tech savvy enough can check out Vanderbeken’s published work on Github. Would-be hackers can do a few things with the script. Firstly, Vanderbeken only hacked his router because he wanted access to his router’s web console without having to input the admin password—which he forgot. So if you are the proud owner of these selective devices, you can be assured that they’re hack-able to both you and others with malicious intents. Chances are most people will rather reset their gateways the easy way by pressing the little red reset button on the back of their device using a pen tip. People looking for an adventure into the world of coding, however, might actually test out the scripts to see if their highly secured network is bulletproof or not.
Another thing to note is that the backdoor vulnerability in these LinkSys and Netgear components are only assessable locally. Meaning, a hacker would have to be in range of your Wi-Fi network for them to compromise your network and personal data.
What Should I Do If I Am Affected?
Quite frankly speaking, unless your neighbor or a passerby knows exactly the type of router you’re currently using, they won’t bother to attempt to hack your network. The easiest solution, if you happen to own one of these vulnerable devices, is to name your wireless network something other than the router’s brand and model.
Often times, the routers come shipped with preconfigured settings which use the brand or model as the default wireless network name. If that is the case, simply log into your router, and change the network’s name. Next, you may also want to upgrade the product’s firmware, but keep in mind that different manufacturers have different firmware upgrade requirements. Check your product manuals or website before attempting to upgrade firmware, because one wrong move can render your router unusable.
If you need further help, contact your office IT support.
Read More