The latest evolution in hacking is here and it’s known as Cybercrime as a Service (CaaS) and it promises to create faster, more powerful hacks, but how?
Well, many people have a need to carry out hacking operations, but don’t have the technical skills to design or even launch these types of cyber-attacks. Therefore, there’s a niche in the market for those who do know how to design a piece of malware to monetize their skills. And this is what the foundations of CaaS are built upon – money and cybercrime.
How exactly does it work, though? And what does it mean for the future of cyber security?
What is CaaS?
Hacking has rarely been referred to as an ‘industry’ despite a few individuals willing to carry out cyber-attacks in exchange for money. However, with CaaS, hacking appears to be turning into an industry which means big bucks and nightmares for computer owners all over the world.
Say, for example, a disgruntled ex-employee wants to sabotage their previous employer’s website to cause disruption to their activities. Now, it’s highly unlikely that this employee would be skilled in the world of cyber-crime, so what would they do? Well, previously they would have tried reading a few online articles about hacking and then given up when they realized how difficult it was.
With the advent of CaaS, though, this ex-employee could easily purchase the software or the execution services of a skilled hacker. Naturally, this is a highly illegal act for both parties, so the resources for these types of services tend to be hidden on the dark web to lower the chances of identification.
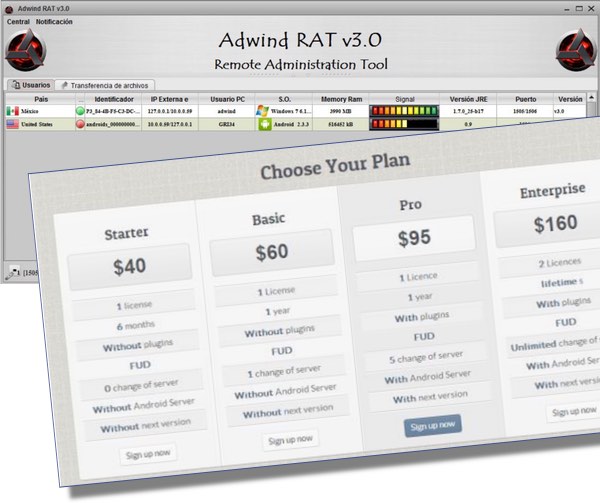
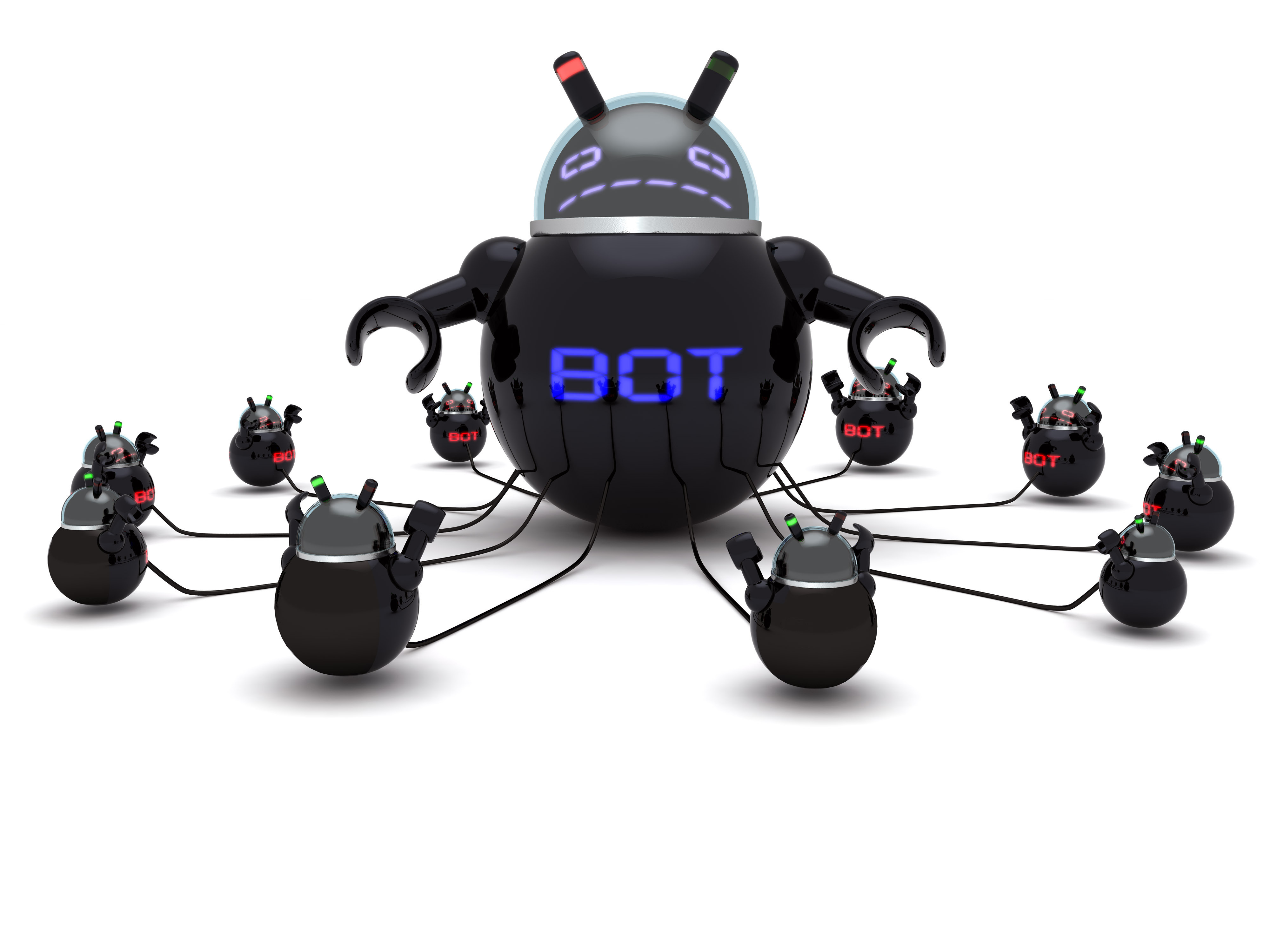
Consumers can expect to find malware kits, access to infected computers and even botnet rentals which allow the initiation of Denial of Service attacks. Therefore, it’s somewhat of an Aladdin’s Cave for someone who is looking for quick, easy access to cybercrime e.g. exploit kits can be purchased for just $50 per day and, believe me, they can cause a lot of damage in one day.
What Does CaaS Mean for Hacking?

CaaS is making hacking much more accessible for the average computer user whereas, before, it was purely the preserve of those who had the skill to design malicious software and carry out sophisticated attacks. This means that we can expect to see an increase in attacks in the future, so safeguarding your networks is more important than ever.
One of the most troubling aspects of CaaS, though, is that when a service becomes a business it drives competition amongst the vendors. And this means that those hackers who are designing exploit kits and various other hacking tools are going to have to up their game to remain in the market.
Therefore, we’re going to see a rapid evolution in the capabilities of hacking tools, so expect faster and more devastating attacks which are harder to stop. In order to protect yourself from these enhanced attacks you’re going to have to ensure that your cyber security protocols enhance visibility of such attacks and prevent them taking hold of your systems.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More