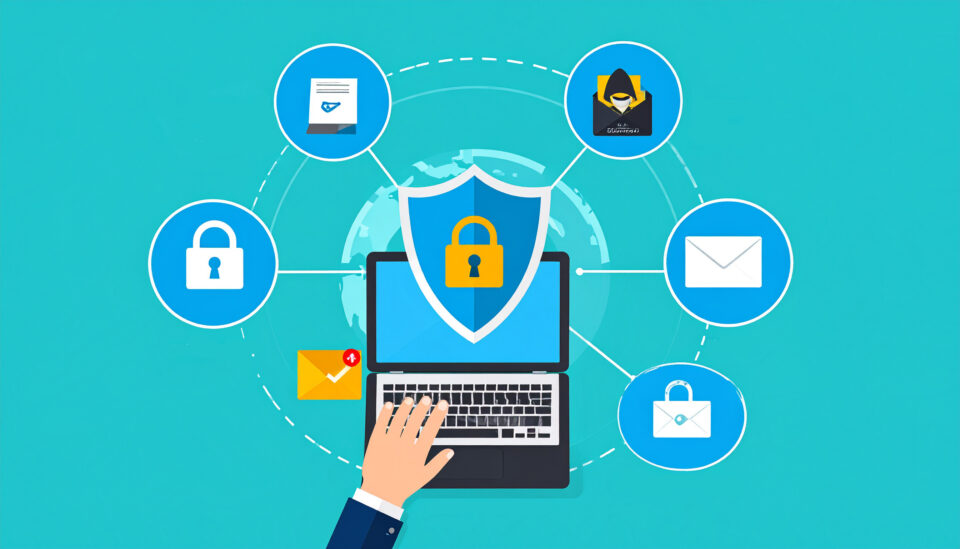
Believing common cybersecurity myths can leave your IT infrastructure vulnerable. Therefore, it’s important to understand the dangers behind these myths.
Myth Busting the Biggest Mistakes You Could Make
In today’s IT-driven business environment, PCs are prime targets for cybercriminals. Regardless of whether you’re working in an office or remotely, your computer will hold highly sensitive and valuable company data. This can take the form of storage drives, access to email accounts, and connections to cloud services. Unfortunately, many PC users rely on outdated or misguided beliefs about cybersecurity – all of which leaves their systems wide open to attack.
Luckily, Ophtek are on hand to debunk seven common myths which could be putting your IT infrastructure at risk of being hacked:
- Antivirus Software is All You Need: antivirus software is crucial, but it’s not a 100% solution. Modern threats will often bypass traditional antivirus tools using phishing emails or zero-day vulnerabilities. Accordingly, if you rely purely on antivirus software without additional security support such as firewalls, regular updates, and careful browsing, your risk of being hacked remains high.
- Only Big Companies Get Hacked: small and medium-sized businesses are increasingly targeted by attackers because they tend to lack the strong security measures associated with larger organizations. And remember, any PC within your business represents a target as it can provide a backdoor into your company’s wider network – it could just as easily be your receptionist’s PC which gets hacked rather than your CEOs.
- Sensitive Info Isn’t Stored on Your PCs: even if you don’t store financial or client data locally on your PCs, it’s likely that at least some of the PCs on your network have the credentials to access this data saved on them. This enables hackers to quickly gain a foothold within your infrastructure and gain access to sensitive data.
- Your Employees Can Spot Suspicious Links: phishing emails are getting harder to spot as threat actors become more skilled in the art of deception. Modern threats often mimic real coworkers, vendors, or official notices from software developers. As even a single accidental click on a cleverly disguised link can put your entire network at risk, it’s vital that you conduct regular refreshers with your staff on the dangers of malicious links.
- Strong Passwords Are Enough: yes, strong passwords are essential, but they’re not enough on their own. Without multi-factor authentication, a stolen or leaked password can give attackers instant and full access to your network. With multi-factor authentication in place, however, you immediately add an extra layer of defense, even if your password is compromised.
- Software Updates Can Wait: postponing software updates, especially for your operating system or browser, is the biggest mistake you can make. Many PC users underestimate just how quickly hackers will identify and exploit these vulnerabilities, leaving countless PCs at risk of being compromised. Consequently, enabling automatic updates whenever possible is the only way to stop falling victim to this myth.
- Your IT Team Handles Everything: it’s your IT team’s responsibility to monitor and maintain your IT systems, but every employee has a shared responsibility to contribute towards IT security. Ensuring that your employees follow simple practices – such as locking screens and not writing down passwords in the office – can make a huge difference to the strength of your network’s security.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More