We invest so much time on our devices that we forget they contain some of our most sensitive information. Here are 3 data encryption options to consider.
Encryption is a method of transforming your data into something that is illegible to anyone without a key. The key, often a long series of letters and numbers, is what returns your data back to its original state so you may access it again.
There are a number of methods for you to protect your sensitive information on your device.
Whole Disk Encryption
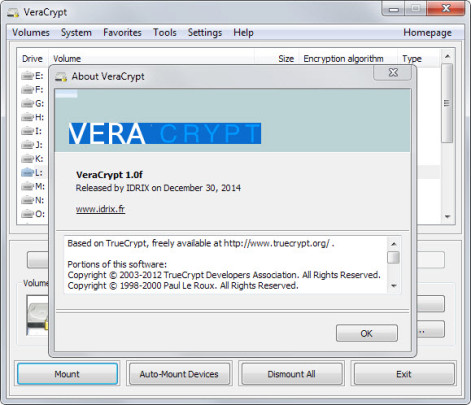
This type of encryption encrypts your entire drive and everything on it. You can encrypt any number of volumes or drives that are connected to your computer. If your hard drives are physically stolen out of your computer, the thieves wont be able to access them without the right key. This is good practice for businesses that keep their data locally on a server. If you happen to have the Enterprise version of Windows on your device then you have the built in Bitlocker software bundled with your OS for free that can encrypt all your drives. There are also free open source options for you if you do not have the right version of Windows.
A great free option is VeraCrypt, the spiritual successor to the wildly popular but now defunct TrueCrypt.
File Encryption
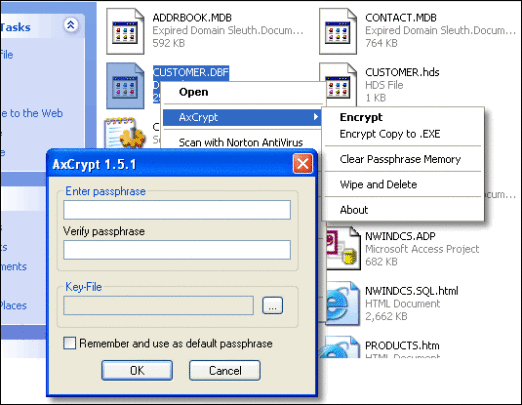
A drawback of whole disk encryption is that your device may take a slight performance hit for being entirely encrypted. For some that is not worth it if they only have a few files or folders to encrypt. If you often have to share your computer with family members or friends this is a great solution. This option lets you encrypt files and folders with just a few clicks. It puts a password on the folder in before allowing access to it. In most cases all you have to do is right click on the file or folder and press the encrypt button. You are then shown steps to follow to complete the encrypting process.
AxCrypt is a great free utility that seamlessly integrates with Windows so encrypting your folders are just a few clicks away.
Compression Encryption
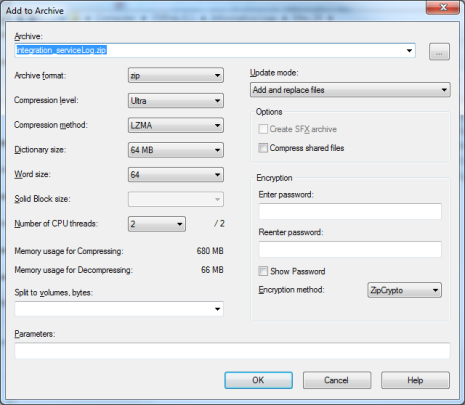
This is very similar to file and folder encryption. It’s possible that most users who have come by a .zip or .rar file already software to see the file contents. What you may not know is that these programs can compress your file size and encrypt that file at the same time. They also seamlessly connect to windows explorer making it just a few clicks effort to encrypt and compress files.
Popular compression software which supports encryption includes 7-zip and WinRAR.
Encrypting your sensitive information is good practice for anyone with critical or sensitive information. Once the device has been stolen or the data accessed by a third party, it’s too late.
For more ways to protect your sensitive business data, contact your local IT professionals.
Read More