Aside from when video connections drop out, is a useful piece of software for businesses. However, the T9000 trojan is compromising Skype’s security.
Aside from when video connections drop out, is a useful piece of software for businesses. However, the T9000 trojan is compromising Skype’s security.
Skype is an amazingly innovative app which has helped make the world that little bit smaller and cost effective. The days of having to pay extortionate rates to call people on the other side of the globe are over. And you can even throw in video conferencing as an added bonus!
Unfortunately, hackers are also innovative and if they discover there’s even a minuscule opportunity to breach a piece of software they’ll pounce upon it. Researchers at Palo Alto Networks have discovered that this is exactly what is happening with Skype and the T9000 trojan.
As Skype is an essential business tool, it was crucial to look through what the T9000 is capable of and how to protect yourself.
The Hard Facts about the T9000
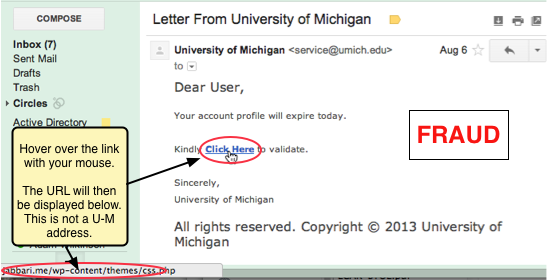
The T9000 trojan is actually an upgrade of the T5000 trojan which was first spotted in 2013/14. The delivery route of the T9000 trojan appears to be through spear phishing emails in the form of infected Rich Text Format (RTF) files which contain exploits for Microsoft Office controls.
Once the malware contained within these RTF files is activated, the following processes take place:
- The first step the malware takes is to check for the presence of the 24 most common security products e.g. Kaspersky, AVG and McAfee
- The malware is then installed onto the system’s hard drive and performs a number of checks which allow the T9000 trojan to relay information about the user’s system to the control and command centre supporting the attack
- Three plugins (tyeu.dat, vnkd.dat and qhnj.dat) are then decompressed and executed on the infected system
- The tyeu.dat plugin is the one which will hijack Skype through a user prompt next time Skype is started
If this user prompt is authorized then the T9000 can begin spying on the user’s Skype sessions. This allows the T9000 the perfect opportunity to steal screenshots, audio and video data from the infected system.
The vnkd.dat plugin also works away in the background with its main intent being to steal files from the hard drive or any removable devices. Finally, the qhnj.dat plugin gives the control and command center the opportunity to send commands to the infected computers and spy on any user activity.
Protecting yourself from the T9000
The T9000 trojan is a very sophisticated piece of malware which threatens the security of your system on a number of different levels. The key to avoiding infection, as ever, is to practice good security methods.
Training staff on the dangers of unknown and unusual attachments is paramount, but your staff are only human and mistakes will no doubt be made. The T9000, however, is not infallible, so if your business has professional network security in place the threat will be limited or stopped in its tracks.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More