Malware causes many security concerns, but, just recently, hackers have been targeting the Ukraine’s electric distributors to bring havoc to power supplies.
Malware causes many security concerns, but, just recently, hackers have been targeting the Ukraine’s electric distributors to bring havoc to power supplies.
Instead of merely targeting secure data such as financial and classified information, the authors behind the malware – known as Black Energy – are infiltrating the systems at leading energy suppliers to cause widespread disruption.
To better understand the serious risk that this can bring to a business, we decided to investigate exactly how the hackers are executing this attack.
What’s a Spear Phishing Email?
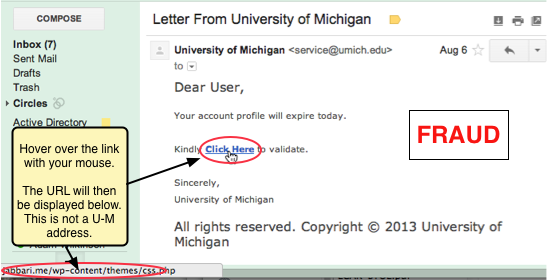
The malware attacks in the Ukraine have been carried out with the help of a spear phishing email, but what exactly is this?
Well, it’s pretty similar to your standard phishing email, but a little more sophisticated.
A spear phishing email attempts to deceive you by demonstrating a level of familiarity. For example, instead of starting with Dear Sir/Madam, it’s likely to use your actual name e.g. Dear Ben. And it’s also likely to make a reference, in some way, to an event in your life e.g. marriage, online purchase etc.
And where do they pull this information from? It’s pretty simple, social media sites and pretty much anywhere online where you may upload personal information.
By demonstrating some familiarity with yourself, the hacker is able to lower your defenses and increase their chances of extracting information and potential access to your system.
How Did Black Energy Gain Access?
The Black Energy malware attack involves a spear phishing email which contains a seemingly innocent Excel document. Once this document is opened, the recipient is advised to enable macros, but this is a big mistake!
Once the macros are enabled, the Trojan downloader loads up malware which is capable of executing files, keylogging secure data and taking screenshots. This backdoor into the infected system is operated through a Gmail account and contributes to the difficulty in tracing the hackers.
The Effect on Power Companies
Ukrainian power companies such as Prykarpattyaoblenergo and Kyivoblenergo have been attacked by Black Energy and suffered widespread disruption to their operations. The biggest impact of this has been the resulting outages in power for local regions.
Although it’s not been confirmed or denied, it’s unlikely that the Black Energy creators were actively involved in flicking the power switch off. It’s more likely that infected systems struggled to operate and are unable to boot correctly or freeze.
The cumulative effect of these symptoms is that the energy companies are unable to run their system as intended and things start to go wrong. In several cases, this has resulted in the reported power outages.
Obviously, energy is essential everyone in the surrounding community, so this threat is being taken very seriously.
Combating Spear Phishing Emails
Spear phishing emails appear very genuine, but their deceptive power should not be underestimated as the Ukraine has learned. Business staff need to remain vigilant of all emails coming into their business in order to maintain security.
The authors behind Black Energy are yet to be identified, so the threat of them (and others like them) striking again remains a very real risk.
For more ways to secure and optimize your business technology, contact your local IT professionals.