We use the internet on a daily basis and visit countless websites along the way. But they’re not always the real deal. And sometimes they can be malicious.
The internet is a wonderful place and the websites that make it up can make a real difference to your business. Sadly, this opportunity is often subverted by criminals and hackers to be much more dangerous. And, with each new step the internet takes, there are even more chances for these criminals to take advantage of. For example, online payment sites such as PayPal have allowed businesses to work closely with their customers to deliver hassle free payment methods. But, with a financial element at play, these sites have been heavily targeted.
Hackers have developed sophisticated techniques for setting up fake and scam websites, so it’s difficult to identify these fraudulent sites. However, by learning a little more about these techniques you can learn how to identify fake and scam websites.
What Do You Need to Look Out For?
There are a number of tell-tale signs adopted by fake and scam websites, so make sure you take note of the following when browsing online:
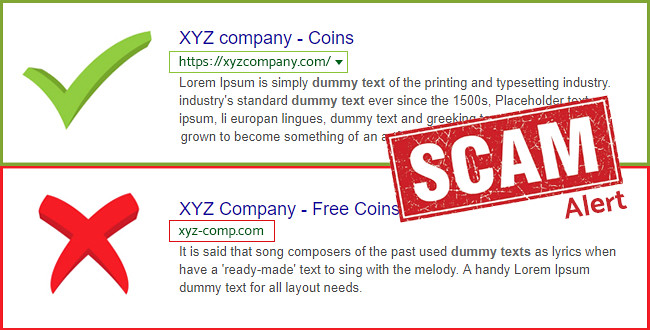
- Always Check the URL: The address bar of your browser is one of the most important tools at your disposal when trying to identifying a fake website. The URL listed in the address bar may look genuine, but it’s crucial that you always look a little closer. A URL may read, for example, bankofamerica.com.authorization-process.com and look genuine due to the first part of the URL. But, on this occasion, bankofamerica.com is only acting as the sub-domain. The domain that you have actually visited is authorization-process.com.
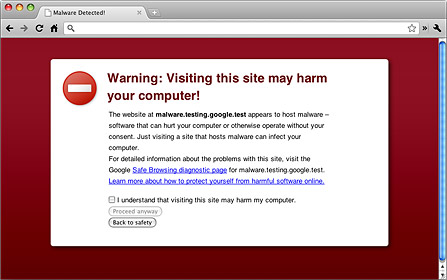
- Secure Connections: You should only ever visit websites that have secure connections. This security is indicated by either a HTTPS prefix on a URL or the presence of a padlock image next to the URL. Without these indicators then the connection will be unsecured and your data can easily be viewed. Naturally, a genuine website will always deliver these security indicators, so if these are not present then leave the website immediately.
- Search Out Trust Seals: Websites that are secure pride themselves on this achievement. And this hard work is rewarded in the form of trust seals which can take the form of Google Trusted Store, Norton Secured and GeoTrust logos. A website with these, and similar, logos is trustworthy. But it’s very easy for a hacker to copy one of these logos on to any website they want. Thankfully, most trust seals can be clicked on to display verified certificate information. If this does not appear then assume that the trust seals are faked.
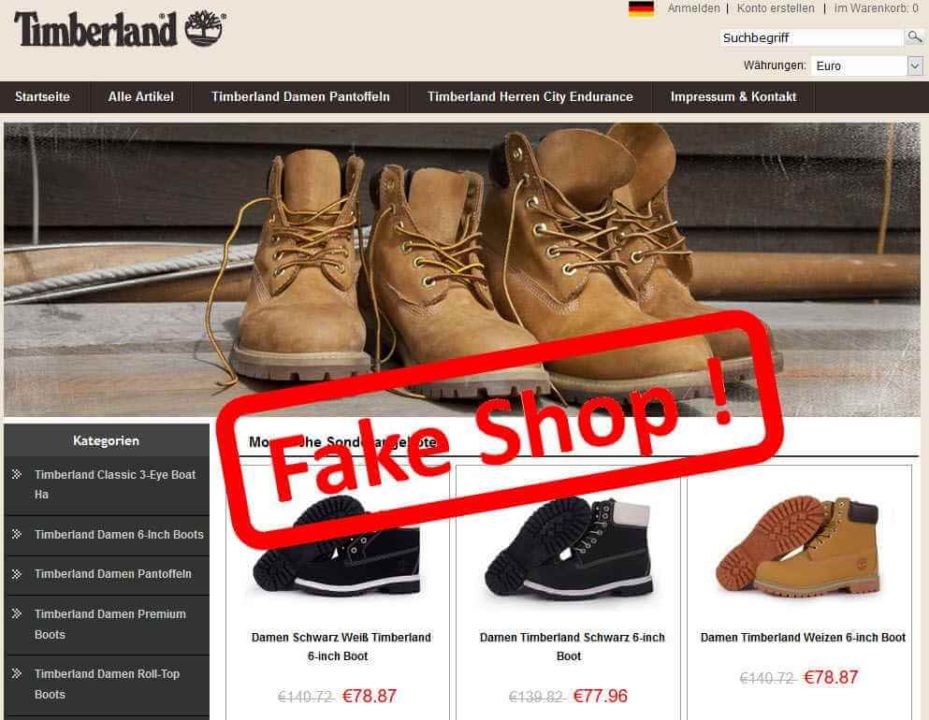
- Check the Grammar: A genuine website will have been written and proofread by professionals. But a fake website will often be designed in a rush and by people whose first language is not English. And the result is a website full of spelling mistakes. So, if you believe you’re on PayPal, but see it mistakenly spelled as PayPal then you can rest assured you’re not on the genuine site.
- Too Many Ads: Online ads are part and parcel of life now. But sometimes it may seem as though there are too many on a website. And this is the calling card of a fake or scam website. The excess adverts popping up are often malicious in themselves, so if you experience more than two when loading up a new page you should tread carefully and begin analyzing the web page further.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More