The Internet of Things (IoT) is amazing, but it’s not perfect and, in particular, there are plenty of security vulnerabilities that you need to know about.
You can barely move without bumping into an IoT device now and, whilst this allows you to be more productive, it also means that the security risk to your organization’s network is increasing. We’ve all heard about how coffee machines can get hacked and it’s these types of stories that demonstrate the extent of IoT security concerns.
Whilst you may rely on a humble kettle rather than a fancy Wi-Fi controlled coffee machine, there are still plenty of IoT security vulnerabilities you need to be aware of. Let’s take a look at of the most important ones you should be aware of.
- Network Services Present a Back Door
IoT devices often come with diagnostic and debugging services built in to help facilitate troubleshooting tasks, but these are often operating on ports which are not secure. Now, maintenance services are probably one of the least likely to be secured pieces of code to be found on an IoT device, so this scenario is highly attractive to hackers. Therefore, you need to make sure that you investigate all potential security concerns on new IoT devices you install.
- Lack of Transport Encryption
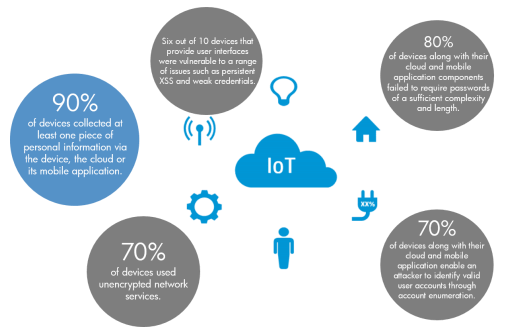
When data is transported across the internet or your local network, it needs to be encrypted to thwart any external parties who are listening to your data traffic. However, many IoT devices fail to employ transport encryption in their data transmissions when sending data – this is estimated to be around 41% of all IoT devices. And this is why you need to make sure that your organization only works with highly secure IoT devices to protect data security.
- Weak Password Protection
The lack of strong password protection is a major security vulnerability when it comes to IoT devices. A good password should incorporate more than 8 characters and these should include numbers, symbols and mixed case letters – more often than not, though, these can often be nothing more than four digits such as an iPhone’s default password protection. And, as we all know, the weaker a password, the quicker and easier it can be hacked by brute force.
- Different Computer Languages Prevent Security
PCs all speak a common language, so getting a network full of PCs to operate on the same network in the same manner is not too big a problem. However, a smart photocopier running on a code all of its own is going to struggle to communicate effectively with the rest of your network. And this means that guaranteeing a secure connection between network devices is more difficult than ever. You also need to consider the fact that many IoT devices fail to receive regular updates, so this has the potential to be a long term security risk.
We’re all still learning about the security vulnerabilities that the IoT is bringing to the security table, so a firm knowledge of the potential pitfalls is vital. By taking note of the above you should be able to improve your security just enough to prevent being hacked.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More