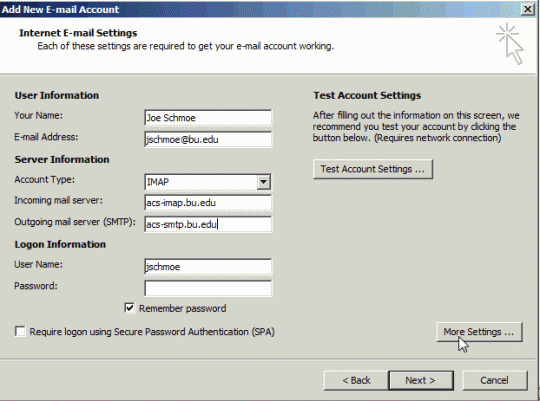
Do you ever worry about someone getting a hold of the data on your computer after stealing it from you? With disk encryption, the information on your computer is unreadable without a key.
You may use encryption to protect specific directories or the entire hard drive. The latter is referred to as full disk encryption.
While there are many applications that perform full disk encryption, we recommend True Crypt. While some may lampoon this recommendation based on an announcement from its old source page, development of TrueCrypt has continued in Switzerland by a team committed not to compromise the software with legal limitations.
After downloading TrueCrypt from the new site, launch it normally if you have a disk burner, also known as a a CD/DVD-RW drive. The disk burner will be required in later parts of the installation. If you do not have a disk burner, there is a workaround that will still allow you to proceed with encryption even though the program does not normally allow it. For more on this workaround to allow to the program to launch without the disk burning requirement, consult the following article.
After you launch the program, click the System button at the top bar and select Encrypt System Partition/Drive.
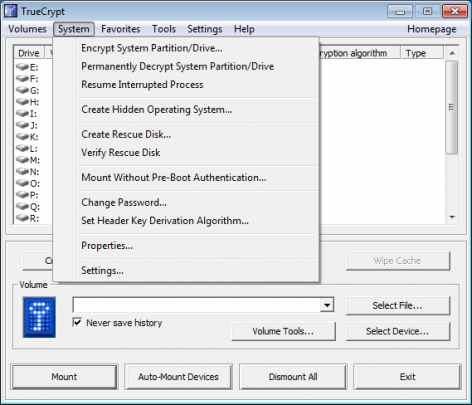
For Type of System Encryption, select Normal. Click Next.
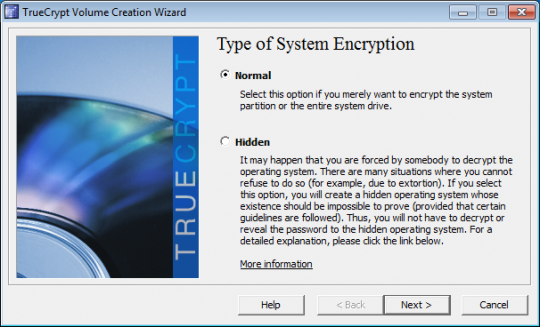
Unless you have a RAID driver or hidden partition at the end of your drive, Yes is the best option when you are presented with the Encryption of the Host Protected Area window.
When you are asked if it is OK for TrueCrypt to make changes to the hard drive, click Yes.
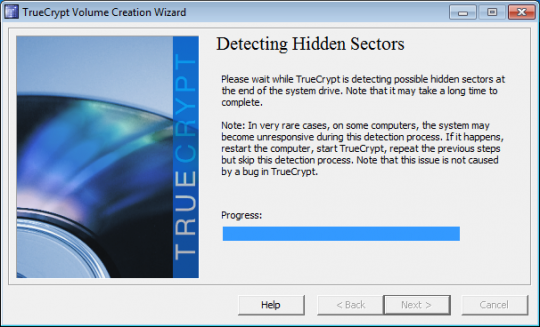
TrueCrypt will then see if there are any hidden sectors at the end of the drive. Click Next when it is finished.
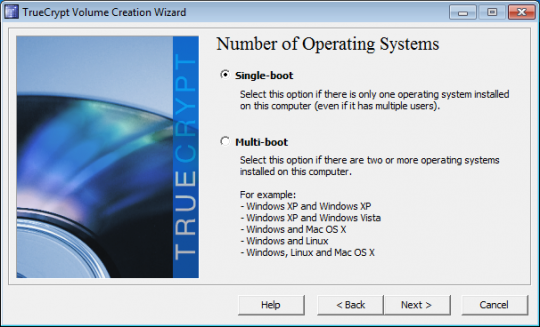
Click Next again after selecting whether the computer has a single- boot or multi- boot configuration. If you are running only one version of Windows and no other operating systems, you will choose Single-boot.
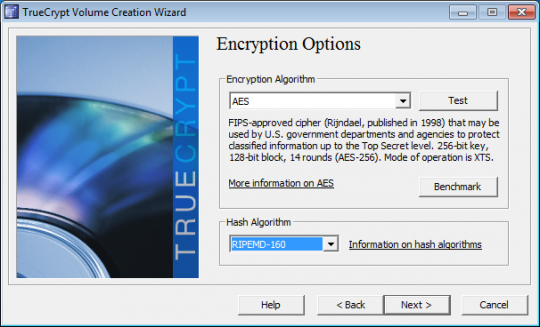
For the Encryption Options, AES is usually a good choice. And full disk encryption only supports the RIPEMD-160 hash algorithm. Click Next.
Choose a password for encryption. Choose a strong password of at least 20 characters. Click Next.
In the next window, make random movements with your mouse for about a minute. TrueCrypt will collect data from these movements. Click Next.
When User Account Control asks if it is OK for TrueCrypt to make changes to the hard drive, select Yes.
Click Next after TrueCrypt generates the encryption keys.
TrueCrypt will then create the ISO image of the Rescue Disk that will be needed if something happens to your boot image. The ISO image will be created in your Documents folder.
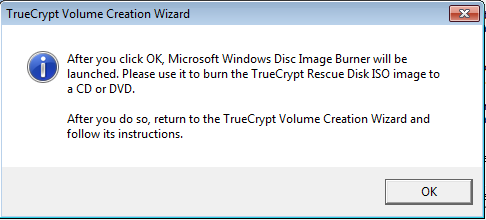
TrueCrypt will next launch the Windows Disk Image Burner to write this image to a blank CD ROM. Because you will need this disk to access your computer if your boot image becomes corrupted, TrueCrypt will not let you get to the next step until you burn and verify the disk. Choose the correct drive to burn the image to, load the blank CD ROM, and click Burn.
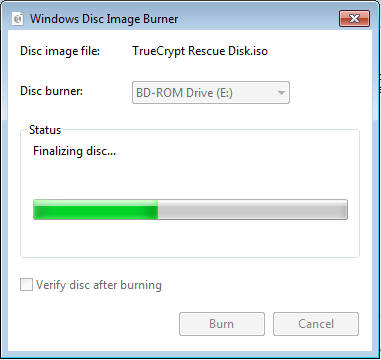
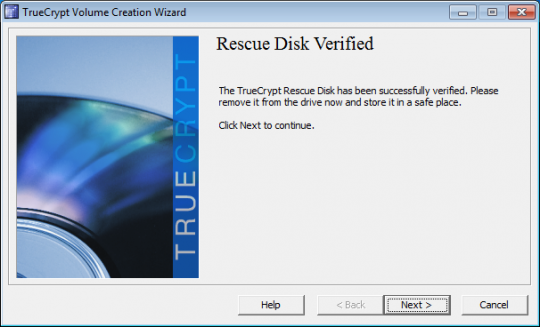
TrueCrypt will verify the disk after burning it. After it has been verified, click Next.
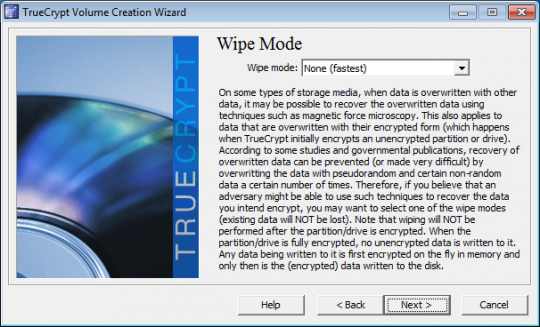
The Wipe Mode allows you to choose how to wipe all traces of previous data that was unencrypted. Typically these were files deleted before this encryption was started. If there was nothing sensitive on this computer that was deleted, click Next.
Next click Test to allow TrueCrypt to make sure everything is working.
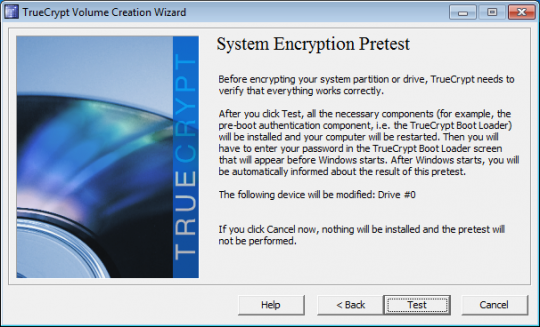
When TrueCrypt displays instructions telling you what to do when the system fails to reboot, it is advised that you print these out for reference. Then click OK. Click Yes to reboot your computer.
After the computer restarts, you will need to enter the encryption password.
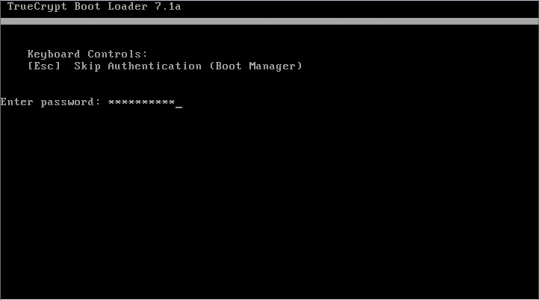
If you enter it correctly, you will be able to log into Windows. After you log in, TrueCrypt will start up automatically. Click Encrypt to start the encryption. Print the instructions showing what to do if the process is disrupted and click OK. When User Account Control asks if you want to allow TrueCrypt to make changes to the hard disk, click Yes. During the encryption, you may do other things on your computer. The encryption should take a few hours.
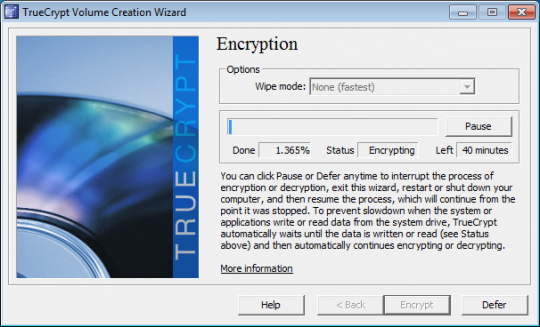
You may pause and defer the completion of the encryption to a later time. But until it finishes, the information on your computer will not be fully secure. When encryption is complete, click Finish.
For more information, consult your local IT professionals.
Read More