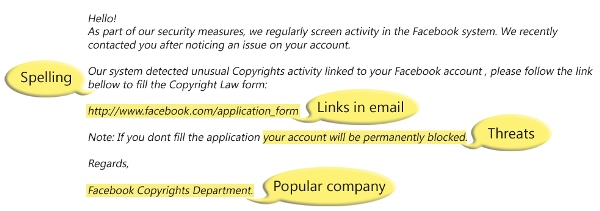
Phishing emails are the scourge of our inboxes and there seem to be more and more each week, so what should you do when you receive a phishing email?
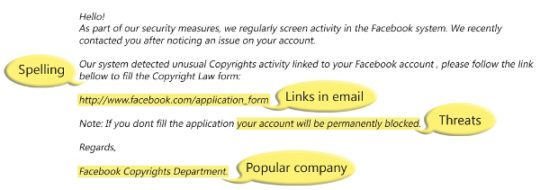
The aim of phishing emails is for the sender of said emails to obtain sensitive information from the recipient. This goal is realized by cleverly disguising the email to make it look as genuine as possible and, therefore, gain the recipient’s trust. Data targeted by phishing emails usually relates to sensitive details including login details and passwords. And this data leakage can cause serious harm to businesses with the average cost of a phishing attack on a medium sized business costing around $1.6 million.
No organization that wants to remain productive and competitive wants to deal with the chaos of a phishing attack, so we’re going to take a look at what you should do when you receive a phishing email.
Do Not Open Phishing Emails
The best way to avoid the dangers of phishing emails is very simple: Don’t open them! This, of course, is easier said than done as phishing emails have become incredibly sophisticated over the years e.g. spoofing email addresses. However, if for any reason whatsoever you do not recognize an email address or there’s something unusual about the email subject then it’s always best to err on the side of the caution. Instead, move the cursor away and get your IT team to investigate it before going any further.
Leave Links Well Alone
Opening a phishing email isn’t enough, on its own, to activate the malicious payload, but it’s very simple to do so. Phishing emails often contain links which, once clicked, send the user to malicious websites where malware is automatically downloaded to the user’s PC. This malware is usually very discreet and is able to run silently in the background where it is able to log keystrokes or even take control of the user’s PC. So, remember: if you don’t recognize the sender of an email, it’s crucial that you never click their links.
Don’t Respond
Phishing emails will often try to gain your trust by establishing a connection, so you need to be mindful of these deceptive tactics. By hitting the reply button, for example, you’re demonstrating to the hacker that not only is your email account active, but that you’re willing to engage. And, if a phone number is provided, never ever ring it as it will involve further social engineering and potentially a very high phone charge to a premium member. It may be tempting to respond, but always say no and move away from engaging.
Report the Email
Any form of hacking represents a serious threat to the security of your organization, so it should be every employee’s duty to report a phishing email as soon as possible. This allows your IT team to analyze the email and its contents before taking action. This could be as simple as deleting it securely or telling you that, actually, it’s safe to open. Ultimately, shared knowledge allows your entire organization to stay on top of phishing emails, so, even if you’ve clicked something you shouldn’t have, report it immediately.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More