Most systems today need to run Java occasionally. With the Java 7 end of life approaching, learn why it’s important to migrate to Java 8 to stay protected.
Oracle has supported Java SE 7 for 11 years now, however, with new developments on the latest version to support current and future technological developments, it has reached its end of life.
As of April 2015, Oracle will cease to provide updates for Java 7, which also includes discontinuing downloads for this version from their websites.
The good news is that existing customers are entitled to have continued support for any given security fixes or critical bug issues, including long term maintenance for Java 7 and older versions. All this will be available from Oracle’s Java SE Support team. However, it’s best to migrate to the latest version.
Oracle has also included an auto update feature since their January update to help migrate systems from Java 7 to 8.
Why migrate to Java 8?
Java 7 security updates will no longer be made automatically, making any systems running this version vulnerable. We strongly advise all users to switch to Java 8 for continued feature updates and to further close vulnerability exploits. Since vulnerabilities are likely to lead to exploits, its important to secure your computer when browsing the internet on Java based websites.
Java exists to help applications and websites run correctly, which is fantastic. Being dependent on this component can lead to problems. With unpatched or outdated versions of Java, hackers can take advantage of using web browsers to serve up malware by exploiting its vulnerabilities.
By not maintaining frequent Java updates, this only serves to invite attackers to exploit your web browser and computer.
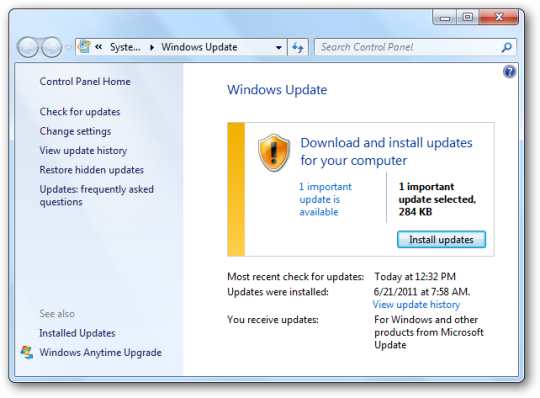
How to update Java and stay protected
Ophtek managed services clients are automatically updated. Follow these steps to update Java manually.
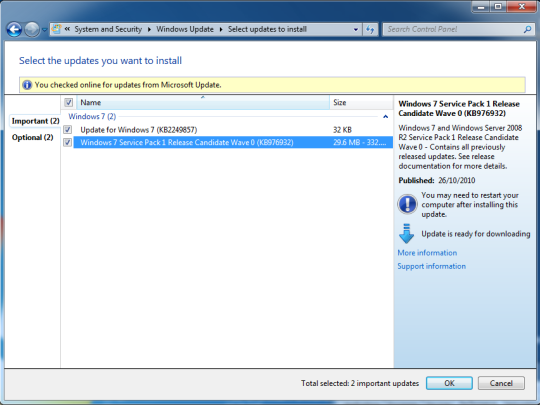
- Visit Oracle’s official website and install Java 8 from there.
- Remove any old versions of Java 7 by uninstalling it.
- Validate the version of Java installed by checking the through the Java website.
Here are more detailed steps on how to install Java updates. Although the Java version shown in this tutorial is older, the method to install and update are still very much the same.
Remember that it’s worth spending a few minutes updating Java on your systems to lock them down from any possible future attacks.
For more ways to protect your office data, contact your local IT professionals.
Read More