We’re frequently bombarded with requests to remember and reset passwords, but this taxing memory drain is causing security fatigue and making us less safe.
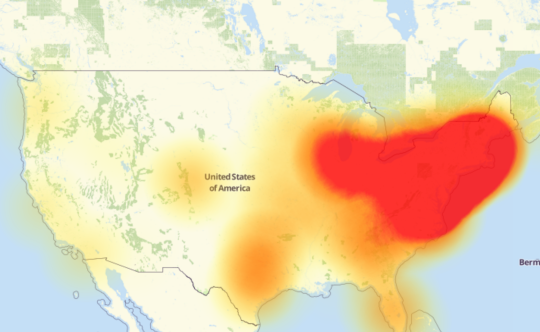
And this security fatigue is causing PC users to take shortcuts with their cyber security e.g. using the same password time and time again across all the online platforms you have to sign in to. Whilst this is a simple solution, it’s also incredibly unsafe as it’s compromising the security of almost all your data.
As this is a security threat which is entirely rooted in the user base, it’s one that’s relatively simple to treat, but in practice it’s one that’s overlooked. Let’s take a look at exactly what’s happening and how you can tackle it.
What Is Security Fatigue?
It seems that not an hour goes by where we’re not prompted to change a password, verify an incoming connection or download a security patch. And this can be a time consuming affair when we’re in the middle of something important, so many PC users begin to experience security fatigue and go for the easy option: ignore everything.
Unfortunately, this puts you at a high risk of susceptibility to hackers. If we go back to our password example, from earlier, we can begin to understand the risks of security fatigue – you won’t just lose one account’s data, but all your data period. And, obviously, overcoming this security fatigue and creating multiple passwords is going to contribute heavily towards damage limitation.
Tackling Security Fatigue

The use of computers in our daily business lives has rapidly expanded in the last 15 years, so the need for security has rapidly increased accordingly. Whereas you once needed just one password to log on your PC, you now probably have to have a whole host of passwords for accessing databases, online portals and emails etc.
As a result there’s no going back to the days of single passwords – we now require around 25 daily to cover all our needs – so we need to learn how we can adapt to this new landscape. And there’s no use dismissing the threat of hackers targeting your data simply because it doesn’t relate to anything important. If a hacker can find even the most insignificant entry point into your network they’ve got a huge head start on causing damage within.
Organizations, therefore, need to work towards lightening the load on their user’s security requirements, but at the same time keep their data secure. This is not an easy problem to solve, but by employing the services of security companies you can gain professional insights on the best way to create a simple security system which reduces the difficulty of decision making and prevents security fatigue setting in.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More