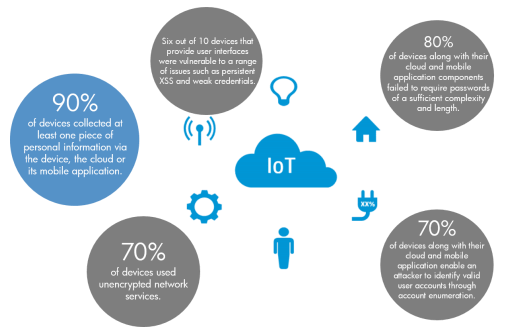
The Internet of Things (IoT) has many security concerns, but perhaps one of the most pressing worries is that IoT devices can be easily hacked for just a few dollars.
A group of elite hackers have recently demonstrated the ease with which a hardware hack can be unleashed to take control of IoT devices. All they require to carry out the hack is an SD card reader, the ability to solder and a length of wire – all in all, this should come to around $10. And once they’ve taken control of the device they can not only exploit any data on there, but also use it as a stepping stone to get further into the network it’s on.
With the number of IoT devices expected to hit the 20 billion mark by 2020, the risk of attacks on these devices is only going to get greater and greater. And, for a business, where nearly every employee will have access to an IoT device, perhaps it’s time to get acquainted with this low cost and easy to deploy attack.
Hacking on a Budget
The hack in question is a flash memory attack and, as such, targets IoT devices which have a flash memory – in particular a form of memory known as eMMC flash. It’s likely that you’ve never heard of eMMC flash, but it’s built into a wide range of devices such as smart TVs, cell phones, tablets and even refrigerators. Just think about how many of those devices are in your organization and connected to your network – that’s right, it’s pretty scary. What, though, is this $10 hack?
Well, the hackers – who go under the group name of exploitee.rs – have revealed that they can gain read/write access to devices by taking a flash memory card and soldering wires to five specific places:
- Data line
- Clock line
- Command line
- Power line
- Ground
This access allows the hackers to start stealing data and to issue commands to the device before taking complete control of it. Once the flash memory card in question is put into an SD card reader, it can then be connected to a PC to glean complete copies of that device’s data inventory. And it’s at this point that the hackers are able to identify zero-day vulnerabilities in the device, vulnerabilities which can be applied to that specific device and any other unit of the same product.
With this information to hand, the hackers are then empowered to launch remote attacks against said device and, potentially, use these infiltrated devices to gain access to the networks they’re connected to. And all of this is possible because hardware manufacturers fail to secure flash memory on their devices, they’re only concerned with creating a front line defense with nothing behind it.
Managing IoT Security Concerns
Hardware manufacturers are slightly off the pace as demonstrated by this budget hack, so for the consumer it’s particularly troubling. As ever, the best advice is to install patches and firmware upgrades as soon as possible. However, when a hardware vulnerability is found it means that it has the potential to leave huge numbers of the same devices – if not all of them – at the risk of being hacked. Therefore, identifying the form of flash memory present in devices may become a major buying point for consumers.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More