Hackers aren’t the only threat to the security of your organization’s Internet of Things (IoT), your employees can be just as culpable for security risks.
Let’s face it, the IoT is a relatively new phenomenon and, even though most of your employees will have smart devices at home, the majority of your workforce won’t be aware of the many security dangers. It’s this lack of knowledge which can lead to major security flaws which leave your network open to hackers and their accompanying chaos.
However, humans have a huge capacity for learning and if you can ingrain the basics of IoT security in the business culture, you’ll find that your employees are soon on top of things. And this knowledge can provide an extra layer of defense, so let’s take a look at how you can provide this.
Ban All Guest Access
Many organizations provide guest access to, at the very least, their Wi-Fi network so that visitors can check emails, liaise with their own staff and, more likely, check Facebook! However, whilst this is a generous gesture, it opens your network up to a whole host of security risks. If there’s a freely available guest network then it’s likely that everyone in your organization will know the password and it can be passed on to any visitors.
Now, you’re never going to know every single visitor to your company and, crucially, you’re never going to know how secure these visitors’ devices are. Therefore, it’s a highly dangerous move to allow your employees to grant free access to any section of your network. The simplest way to combat this and prevent bad security practices is to ban all guest access to your organization’s Wi-Fi. It may seem drastic, but it will really hammer home the security risk to your employees.
Improve the Password Culture
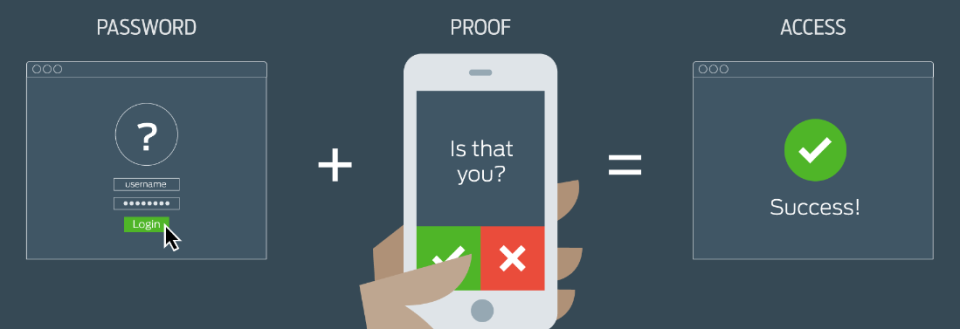
Passwords are one of the oldest forms of computer security, but they’re also one of the most effective. IoT devices, though, have a reputation for coming pre-loaded with highly weak default passwords, so the effort required to hack them is relatively low. Changing not only default passwords, but also regularly changing existing passwords remains a highly important task to secure your smart devices.
Your employees are likely to be highly busy, though, so changing their password will tend to fall down their list of things to do. This is where you, as an employer, need to ensure that regular reminders are sent out to your employees to indicate when passwords require changing. Ideally this should be between 6 – 12 weeks of the last password change and the best way to enforce this is by restricting access to applications if the password is not changed.
Whilst employees will initially grumble about having to change their password and remember a new one, these complaints will soon subside and employees will become compliant with the process.
Regular Training
As mentioned in my opening, the IoT is a new phenomenon and the collective knowledge of your employees will be limited. And that’s why you need to make sure that your staff are given regular training sessions on the importance of IoT security.
Ideally, the IT induction that all new starters take should include a section on IoT security; after all, almost of all your employees will bring a personal smartphone into work and, of course, certain employees will be issued with company laptops and smartphones, so the need for good security practices from the off are vital.
It may seem time consuming to complete inductions and regular refreshing training, but the enhanced knowledge among your workforce will ensure that your networks remain safe from the most simple (yet damaging) IoT security mistakes.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More