Does your computer seem to running much slower than usual? If so, someone may be using your computer’s processing power to mine bitcoins.
This is precisely what bitcoin mining viruses do, yet many of them can be detected with antivirus programs. Malwarebytes is highly recommended for this purpose. Whether your antivirus program is Malwarebytes which we recommend or something else, running a scan every so often will allay infection concerns.
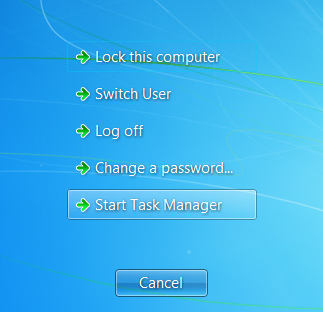
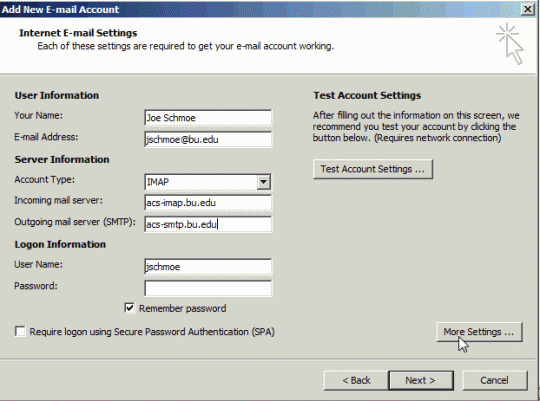
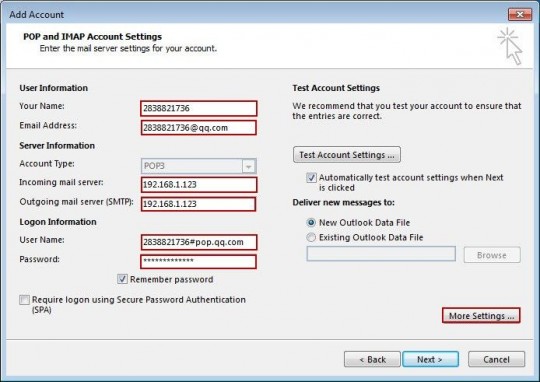
Another way to detect bitcoin malware is by looking at the processes running on your PC. In Windows, hold down the Ctrl and Alt keys while pressing Delete. This will give you the following menu:
Select Start Task Manager from the list of options.
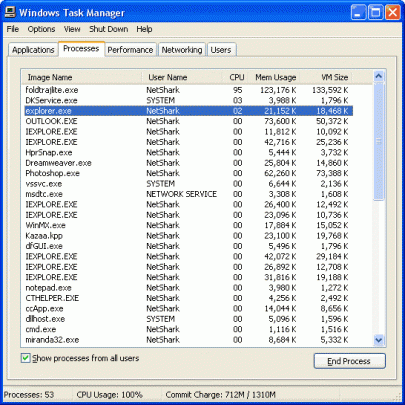
In the Task Manager, select the Processes tab as shown above. Check for any that have unfamiliar names, use a lot of memory or a high percentage of the CPU. You can sort the list by memory and CPU usage by clicking the CPU and Mem Usage column bars at the top. Look up any process with an unfamiliar name on Google.
If the Google search reveals the name to belong to a rogue process, here’s how to remove it from your system.
In addition to being detected by antivirus scanners and causing your PC to use too much of its resources, bitcoin mining viruses can possibly make your computers use more electricity.
All managed services clients are automatically protected against processes that use too much CPU, including bitcoin malware. Although bitcoin mining software on your PC isn’t likely to damage your files, you should always be running a backup to keep your files protected from catastrophic data loss.
For more information, consult your local IT professional.
Read More