With corporate data theft happening frequently, your email may have been stolen without you even knowing. Here’s how to check if your email has been stolen.
What Exactly is at Risk?
The simple answer is data. The power behind stealing data from a company means that your information can get into the wrong hands for malicious use. One prime example is Adobe, who had a large number of their users’ accounts exposed to the public domain. The interesting thing was that these same accounts were being targeted time and time again with the same user credentials, which puts their other accounts at risk. Other sites that have been compromised are mail.ru, Bitcoin Security Forum, Gmail dump accounts, Yahoo accounts, Sony, Tesco and many more.
Compromised information can include your email address, usernames, credit card details and password hints. People often use the same information on other websites as they would have done on their compromised email account making them, yet again, another easy target.
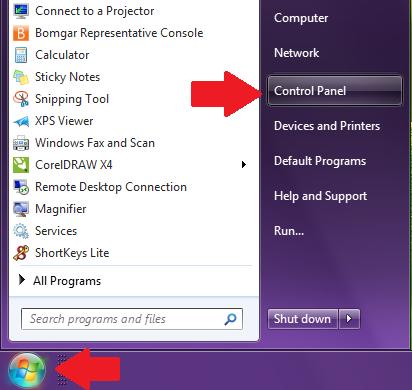
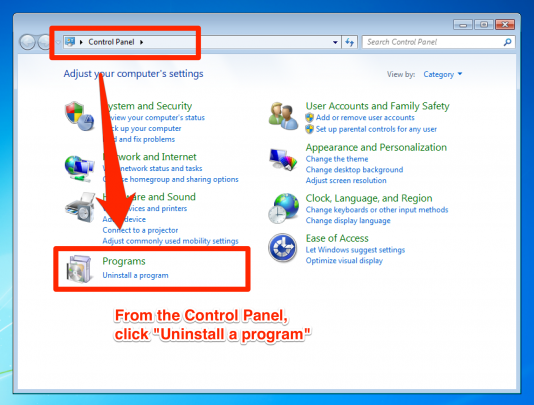
How to Check if You’ve Been Infiltrated
As much as we take precautions with our passwords, secret questions and the like, one needs to check periodically that their details have not already been accessed by unsolicited activity.
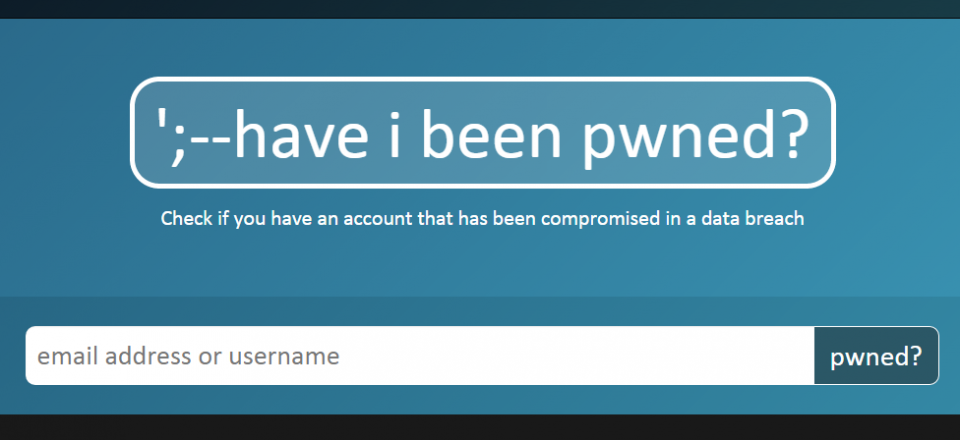
We suggest you check out this free public service, developed by Microsoft professional Troy Hunt, to check if your email or username has been compromised:
If your email has been compromised, you will be advised on this site that it has been “pwned”. Being “pwned” is slang for having your email or other personal information stolen. You can also set up notifications in the event of being “pwned” in the future.
What if I have been “pwned”?
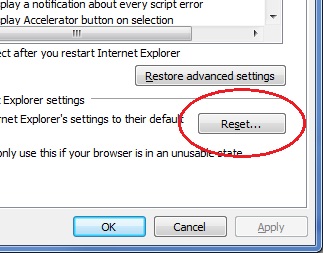
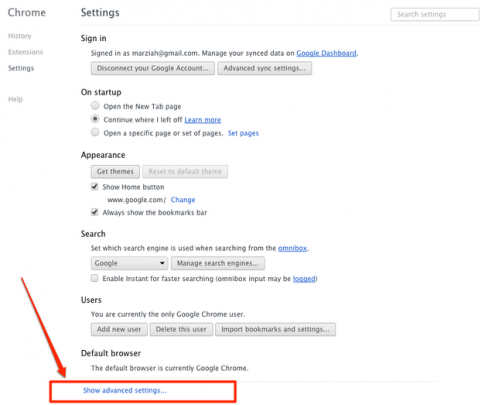
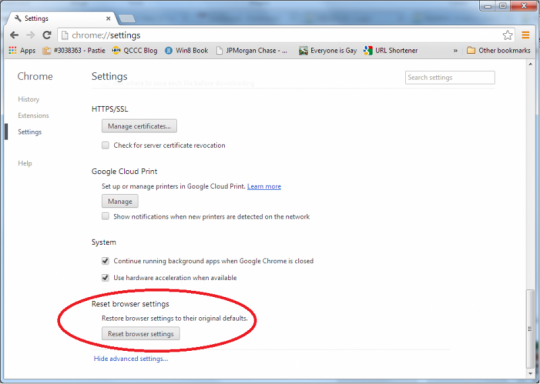
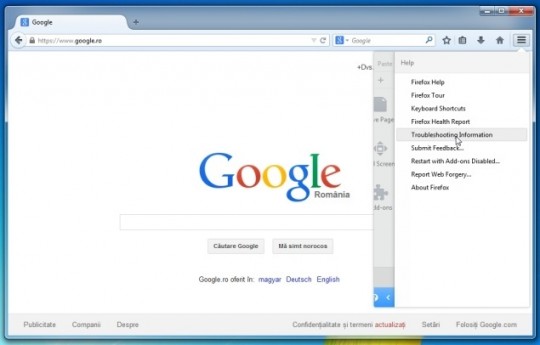
We suggest changing your password ASAP. The best practice is to use different passwords on different accounts. This is especially important for your primary email account, banking, shopping, and whatever else you would consider critical if someone were to steal. If keeping track of your various passwords is a challenge, there are free and secure password managers out there to help.
You can find a good FAQ and a list of other compromised networks as well.
For more tips on securing your privacy and office network, contact your local IT professionals.
Read More