Do you want the option to work from home and access all of your office computer’s files and applications? Let’s cover some options.
LogMeIn was the go to option for remote access software in the past before they started charging for their software. Fortunately, there are free applications that will allow you to remotely connect to your office computer from home.
1.) TeamViewer
TeamViewer, available for Windows, Apple, Linux, or Mobile installs without much fuss and is easy to use.
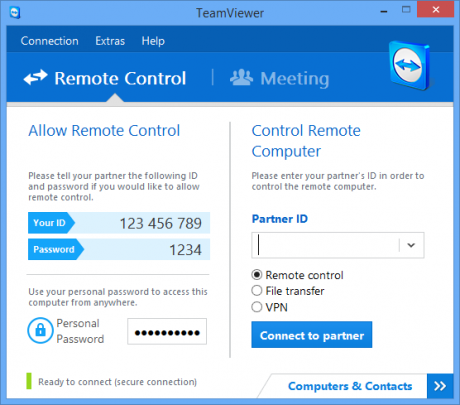
As you see, the TeamViewer window is divided into the Remote Control and Meeting tabs. In the Remote Control tab, Your ID and Password have to be shared with the computer that connects to yours. The Personal Password allows you to access your computer from anywhere at any time provided, of course, it is left on.
In the Meeting tab under Control Remote Computer, you can control a remote computer by entering the Partner ID generated on the remote computer’s TeamViewer window under the Remote Control tab.
2.) Chrome Remote Desktop
Easier to use than TeamViewer, Chrome Remote Desktop does not have as many features. However, the good news is you do not need to have the web browser running to use the app. You will need to have the Chrome browser installed, which we recommend using as your main web browser.
To download Chrome Remote Desktop, go the app page in the Chrome Web Store.
Click the blue +Free button to download the app, and click Add when it asks you to confirm. If you are not signed into Google, it will prompt you to do so.
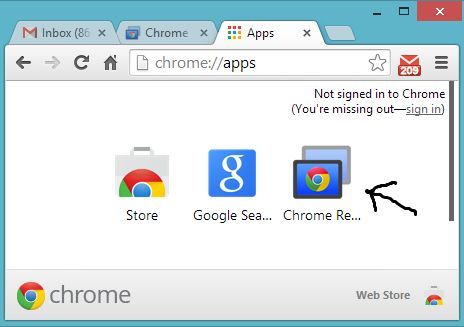
Once installed, click the Apps button under the Chrome search bar, and open the Chrome Remote Desktop App.
Click the Get Started button if it appears.
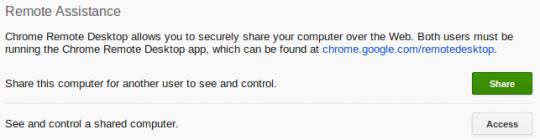
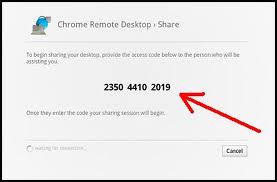
To share your computer with another, click the green Share button.
You will be given a unique access code that the other party will use to access your computer.
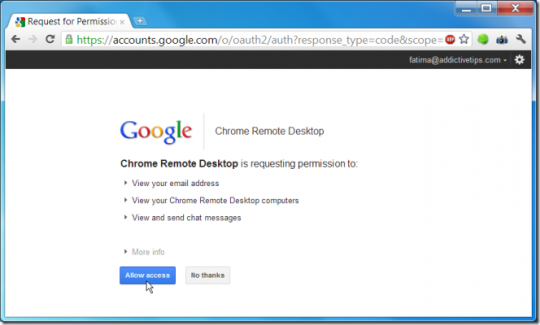
It is recommended that you read the code aloud to the other party rather than type it. Click Allow access to enable the other party’s remote desktop session on your computer.
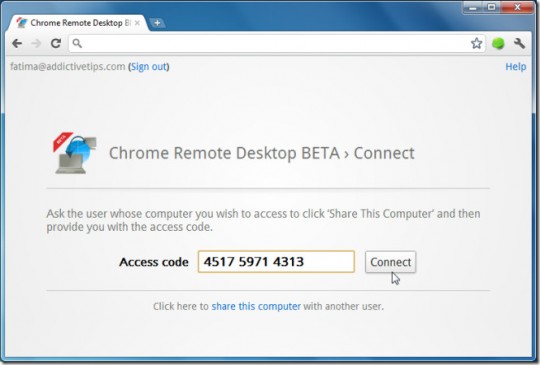
To access a computer available for sharing, open a new tab in Chrome and click the gray Access button instead of the green Share button. Enter the access code provided by your partner whose computer is to be shared.
Click Connect. You can also access your own remote computer you have previously made available for sharing with these latter steps. Just be sure to keep the Access code in a safe, handy place.
The downside of Chrome Remote Desktop is that you cannot perform file transfer with it. Instead you have to upload files to and download them from the cloud.
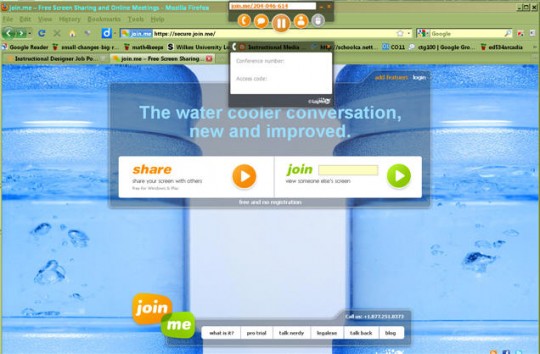
3.) Join.me
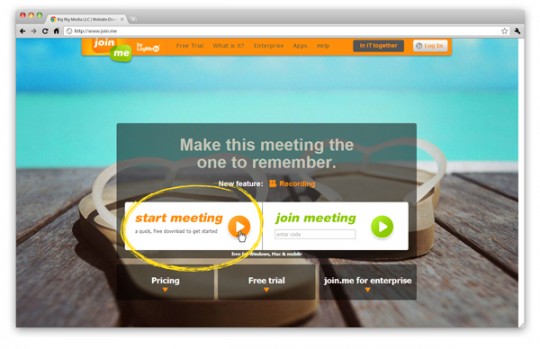
Join.me offers an extremely lightweight remote desktop app that is simple to use. If you opt for their basic plan, it’s free. To share your desktop, go to their homepage and click start meeting.
A number will be generated for your sharing session. It should be near the top of the screen in orange.
Give this number to the party on the other side. They will be able to use this when they connect to your computer by clicking join. Like TeamViewer, join.me is capable of file transfer, and you do not need to register or create an account to use it.
Which should you use?
Because of its inability to do file transfers and the Google account login requirement, Chrome Remote Desktop offers fewer comparative advantages than the other two remote desktop apps.
Between TeamViewer and join.me, the latter is slightly easier to use. However, TeamViewer offers more features that the free version of join.me. These include co- browsing, whiteboard, and video/ webcam capabilities These extra features more than offset the streamlined, ergonomic interface of join.me and warrant TeamViewer as the recommended free application for remote access.
For more information about remote access or other issues concerning your home or office computers, consult your local IT professional.
Read More