Microsoft has recently announced the preview version of Windows 10 for the general public. Here are our favorite Windows 10 features for businesses.
At a glance, it looks very much like a hybrid of Windows 7 and Windows 8, with some colorful Apple elements thrown in. We’ve decided to discuss here some of our favourite features of Windows 10 which may be of interest to businesses and professionals:
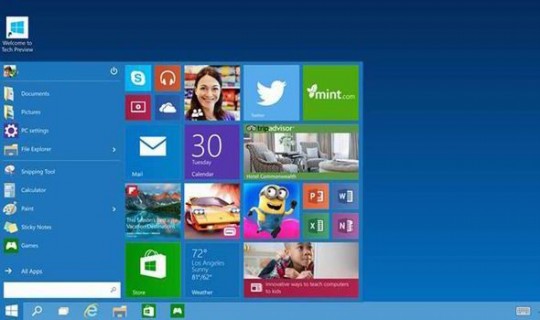
The return of the Start Menu
That’s right, the start menu, which was absent on Windows 8, has been reintroduced into the OS. It’s similar to the former start menu in Windows 7, yet it includes live titles like in Windows 8 and attractive “Apple-esque” looking tiles. You can also resize it!
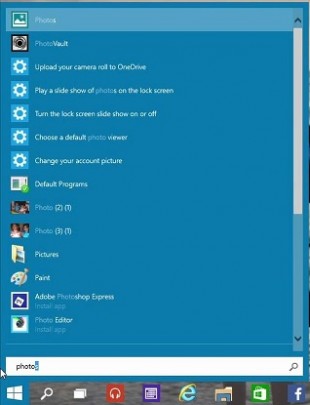
Extended search functionality
Within the start menu, you will be able to search anything from your current PC or device, such as files or Apps, as well as any search results from the internet.
Windows 10 Universal Apps
Microsoft is following the Apple App Store trend by unveiling their own Windows Universal Apps, which we guess will be compatible across various devices, including phones. Older Windows Apps should still work on Windows 10.
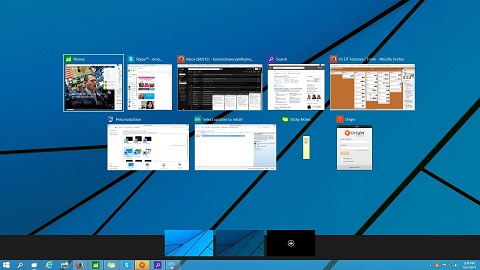
New multiple Task View and Split Screen features
Microsoft have done away with Windows 8 Task switcher and have introduced a brand new Task View, which will allow users to switch between virtual desktops. This makes it a whole lot more user friendly and allows you, for instance, to separate your work desktop from your home desktop. It also splits the screen up into four quadrants to make it easier to segment your work.
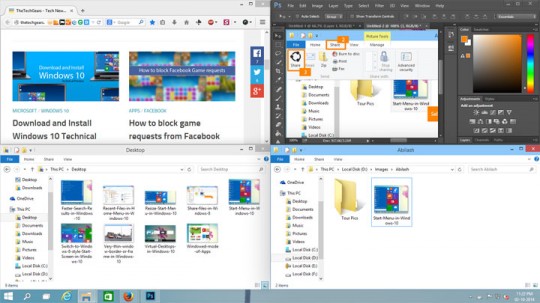
Snap Assist feature
This is another new feature which allows you to arrange (“snap”) your Apps and windows into tiles or new screens.
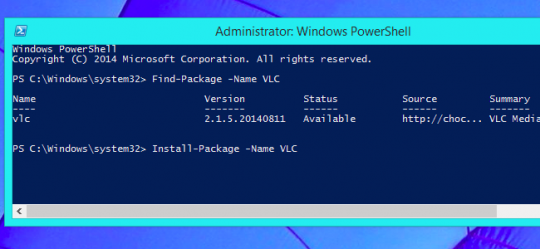
Package Manager “OneGet”
Following in the footsteps of the very popular Linux based package managers, Windows 10 will allow you to install programs directly from the command line. It may not sound exciting but imagine avoiding the 10+ windows of Next-Next-Next to get common software up and running. Deploying programs on many systems also becomes much more manageable.
Business functionality features
On Window’s 10 Technical Preview for Enterprise, there is said to be features that are currently under development which have not all yet been included. Some features will include specific business functionalities such as DirectAccess, AppLocker, BranchCache and Windows To Go. We can only imagine that data security and asset management will be at the top of their list.
Final Thoughts…
Now you have a run-down on some of the popular features for the Windows 10 preview. It’s available for download, but be sure to do this on a test computer or VM.
Since the negative backlash on Windows 8, Microsoft is looking for feedback to improve on their new OS before selling it to the market. In our opinion, this is a great thing as they are listening more to the consumers’ needs and practical solutions. Since most businesses and professionals depend on some Windows operating system, this is an opportunity to provide constructive criticism for an improved OS to be born.
For more information about whether Windows 10 is right for your business or practice, contact your local IT professionals.
Read More