
Intel is constantly striving to push the capabilities of desktop computers and their 72 core processor promises to deliver amazing performance.
This chip – known as Knights Landing – is part of Intel’s Xeon Phi processor family and will start being shipped with select workstations in early 2016. It’s rumored to be Intel’s most powerful chip yet, so this could be the final step in bringing the power of supercomputers to businesses of all sizes.
As this could make a huge difference in how your business operates, I’m going to take a look at why the Knights Landing chip should be on your radar.
Working with Workstations
Almost all businesses have desktop PCs and these are adequate for uses such as word processing, data entry and running general admin tasks. However, the power contained in this hardware is not sufficient for everyone. And that’s where workstations step in.
A workstation may look like a desktop PC, but it’s considerably larger. This increase in size is indicative of the processing power required for complex computing tasks e.g. video editing, engineering programs and state of the art graphics software.
But what exactly can Intel add to the current workstation landscape?
The Power of Knights Landing
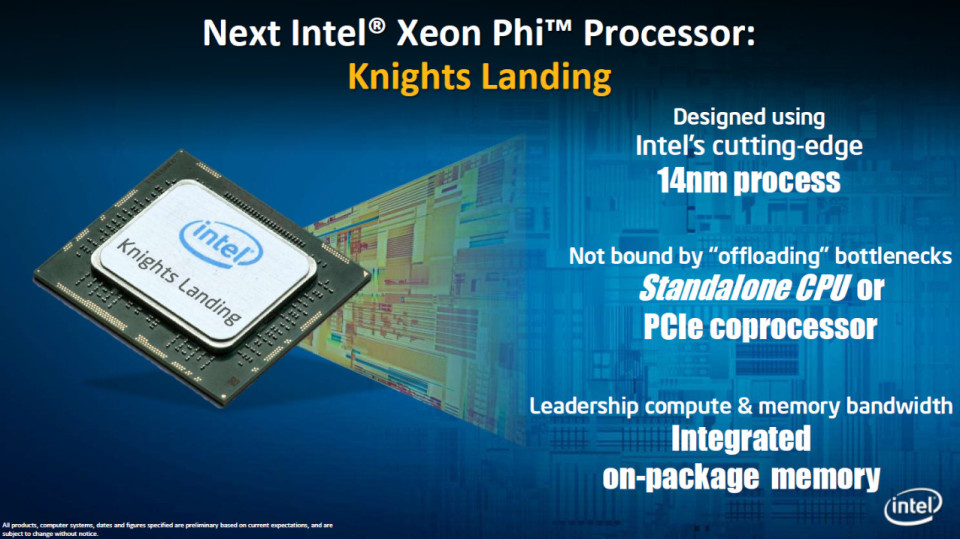
Knights Landing will be able to take on huge workloads that a standard PC would barely struggle to get to grips with before grinding to a halt. It can achieve this because the Knights Landing processor is capable of producing over 3 teraflops of performance power.
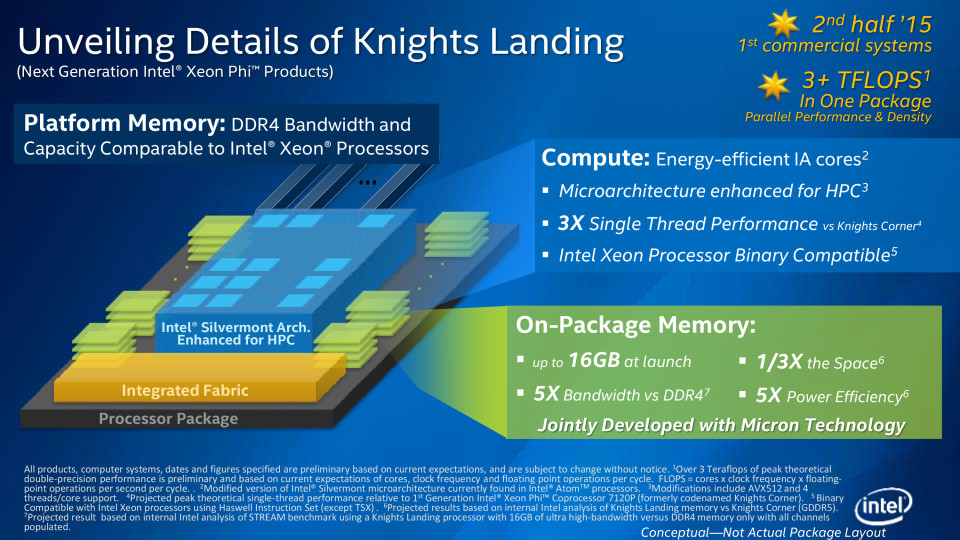
Knights Landing – comprised of standard x86 processors and new, specially designed processors – will bring a huge 16GB of MCDRAM memory which will boost your applications’ performance in a way you didn’t know possible. In fact, this memory will deliver nearly five times more bandwidth than DDR4 memory which is currently considered state of the art.
These figures, of course, sound very impressive, but what will they bring to the market?
What Will Knights Landing Do?
Scientific researchers need to carry out fiendishly complex calculations to aid their research, but the computing power required to process these sums is exceptionally high. So that’s why the scientific community will be Knights Landing’s first port of call.
Currently, these scientists would need access to a Xeon Phi supercomputer to even write and test their calculations. However, the advent of Knights Landing presents an opportunity for scientists to tinker with their code on PCs before running it on a supercomputer. This will free up resource heavy supercomputers purely for the high-end number crunching.
But working out these calculations is only the tip of the iceberg. Knights Landing’s raw power will help bring high performance computing to the masses. Graphic designers and video editors will suddenly find that they have the power to deal with big data. This will transform small businesses and freelancers’ output and capabilities to a level previously considered unthinkable.
When Should You Purchase a Knights Landing Workstation?
Costs and availability of a Knights Landing workstation are going to seriously affect whether you can purchase one anytime soon. It’s currently seen more as a tentative step into this new frontier of computing rather than a product for the masses.
However, over time, it’s highly likely that this technology will become more available and affordable for consumers. It, therefore, remains a viable game changer to businesses who work with high-end data.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More







