With more regulatory commissions requiring encryption and privacy being a hot topic, it’s important to understand what encryption is and whether you need it.
Encryption is nothing new; in fact, it was used thousands of years ago during the ancient times in Egypt, encryption was used to hide messages in the tombs of kings. It has been used time and time again by different civilizations, and was even applied through the Word Wars to keep messages hidden away from the enemy.
However, in most recent history from the 90s, encryption has been adapted to be used as a security measure on computers and over the internet.
Nowadays it has become ever so important for financial institutions, healthcare practices, legal, law and governmental offices to apply encryption into their systems. This allows them to secure their information, whilst remaining complaint with data protection standards.
What is Encryption?
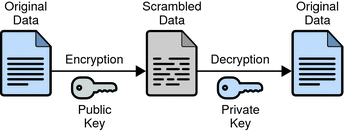
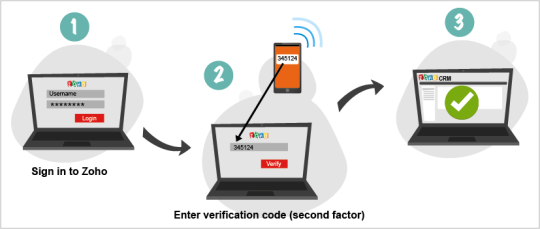
A basic encryption implementation explained by Oracle.
As you may now understand from our examples listed above, encryption obscures information, away from prying eyes. More specifically, it does this by making data unreadable to outsiders. In technical terms, a mathematical formula is used to scramble the data, which appears as gobbledygook to anyone else reading it. Only the person who holds the key can, in a sense reverse the mathematical formula to unlock and read the data.
Why encrypt your data?
Data encryption ensures that you can deter hackers and lessen the effect of being a prime target of criminal activities, looking to intercept your data. Often the most valued data is your personal information. Just think of how many emails contain passwords to accounts, medical reports archived, interests displayed, and an insight into all of your personal activities.
With all this, a hacker can spear-phish you and later target you again, with the likelihood of succeeding. This will be done by simply using your details against you, without you even realizing it.
Therefore, it is extremely important to encrypt your information if you work anywhere that handles sensitive information, confidential emails, and if you travel with a notebook or similar device that uses the Internet.
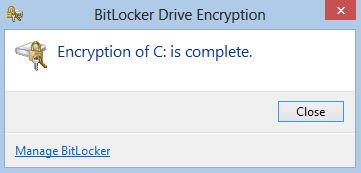
Encrypting your hard drive
Hard drive encryption can help to protect your computer from unauthorized access, since a user needs a key in order to read it.
There are many programs that can help to encrypt your disk such as TrueCrypt, Bitlocker and RealCrypt.
To learn more about Hard disk encryption, please read our how-to article here.
Encrypting your email
Email is used by just about every person who uses a computer, smart-phone, device and works at a business, or all of the above!
Did you know that your email can be intercepted and read by anyone who has access to the right tools?
A good tool to use is called PGP (Pretty Good Program), which can encrypt your email. In order for this to work, both sender and receiver need PGP installed. The sender will generate a random key, and once the encrypted message is sent and received, the recipient can unlock it with a key generated by their PGP plugin.
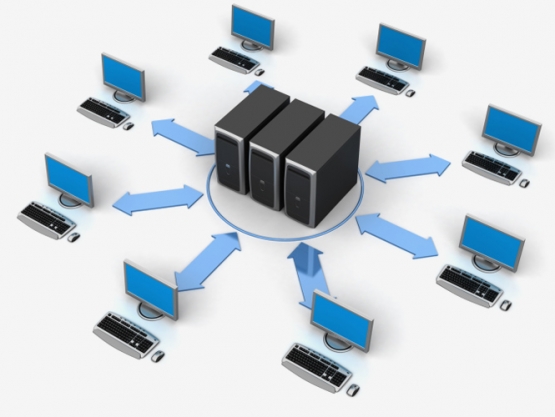
Encrypting your internet connection
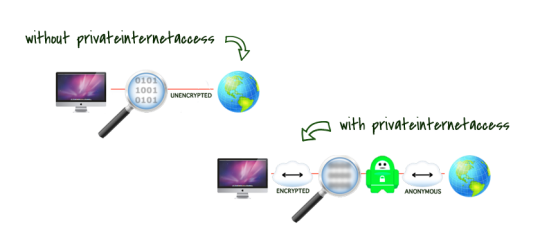
How VPN works as explained by Private Internet Access.
As the name suggests, VPNs (virtual private networks) are a safe way to connect to a private network or to access the internet.
One good analogy is comparing a VPN connection to a walled tunnel, where outsiders would “hit a wall” along the tunnel, unable to infiltrate and access what goes through the tunnel. Whereas a usual Internet connection can be likened to your data travelling on a street and potentially be seen or accessed by outsiders. This is where the term “VPN tunnel connection” comes from. Within this tunnel, all of your data is encrypted. User can access a VPN by having a VPN client installed and accessing a login prompt that will securely authenticate them.
Some VPN clients worth considering are ProXPn, TorVpn, TorGuard, Private Internet Access and WiTopia.
There’s so much to consider with encryption. Just about everything can be a risk without it, so be sure to adopt this secure technology into your business practice to maximize your security.
If you need support and advice with your encryption needs to stay compliant, contact your local IT professionals.
Read More