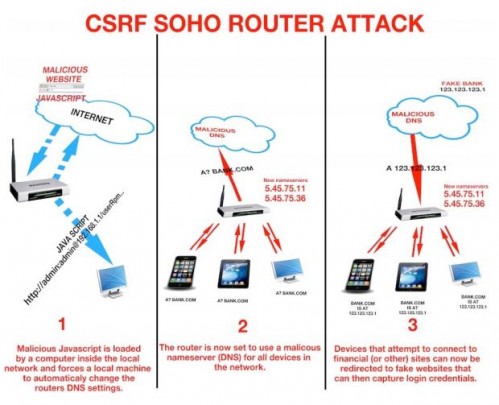
A recent Windows 7 update meant to make the transition from Windows 7 to Windows 8 easier has been causing systems to freeze up according to many user accounts online. Microsoft released this update on April 22nd as KB2952664. There have been updates in the past which have caused the operating system to lock up, freeze or malfunction such as this Microsoft Security Essentials update for Windows XP which was pulled by Microsoft after user’s started having issues.
Although the patch has been labeled as an “important” update on some systems and “optional” on others, it isn’t necessary to keeping Windows 7 operating properly. It is best for users to hide this update completely.
If you haven’t installed it yet, here’s how you can avoid this update and avoid issues with your Windows 7 System:
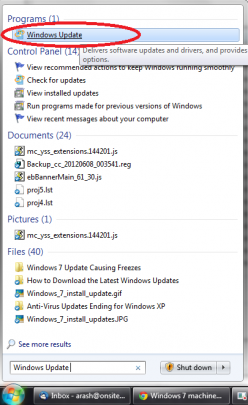
Go to Start and type “Windows Update” without the quotes in the search box. Click on Windows Update at the top of the list:
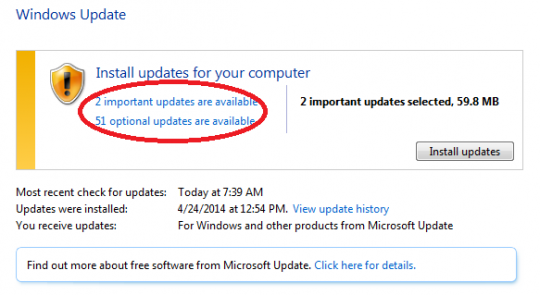
You will need to look in both the Important Update and the Optional Updates for this patch:
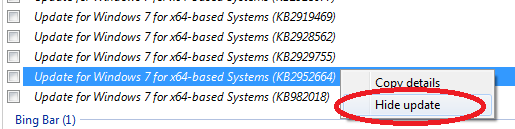
Search for the patch with id KB2952664 in the updates list, right click on it and select Hide Update:
If you have already installed the update, or don’t see the update listed in the Important Updates or Optional Updates section, you may need to uninstall it manually.
You can do this by going to Start -> Control Panel -> Programs and Features -> View Installed Updates. Then find the patch with ID KB2952664, right click on it and select uninstall. Then follow the steps above to hide it from future updates.
All monthly maintenance clients will have this done for their systems during their next update cycle. For further support or questions about this issue, contact your local IT professionals.
Read More