Many businesses are struggling to combat the increasing sophistication of hackers. However, the key to data security may lie in multifactor authentication.
When firms such as Apple are struggling to reduce the threat of hacks which spell disaster for their employees, it underlines the ease in which hackers can gain access to sensitive data. One way that you can put obstacles in the way of potential hackers is to implement multifactor authentication (MFA) into your business.
You may be wondering what MFA is, so let’s take a look!
The Basics of Multifactor Authentication
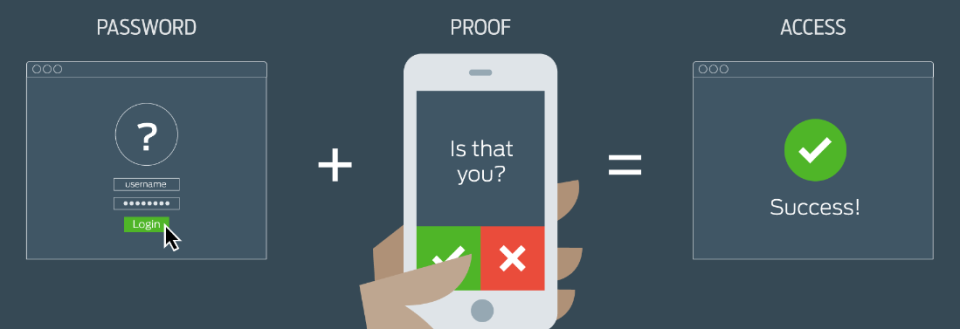
Whilst MFA may sound both a bit of a mouthful and incredibly technical, the truth is that it’s a simple concept. Whereas you may currently require your employees to log on to your system with a password, MFA takes it a little bit further.
What MFA demands is that at least two user credentials need to be combined to provide access. The credentials employed in MFA tend to center around the following categories:
- Password – Yes, that’s right, the good old fashioned login/password combination still has a place in the 21st century!
- Authentication Token – A small device which users carry such as a swipe card. Using this device will allow users to access your system.
- Biometric Authentication – This is where things start to get really futuristic as it relates to forms of genetic verification e.g. retina scans and fingerprint recognition.
What’s Wrong with Just Passwords?

Passwords have been in use with computers for as long as we can remember; we suspect that they will also continue to be here for some time. However, on their own, they represent a security risk.
The main problem with a reliance on passwords is that they have to be stored somewhere on a database. Immediately, this presents the threat of all your passwords being compromised if a hacker manages to access the database. And, as mentioned at the start of this article hackers are becoming very sophisticated.
It’s relatively simple for hackers to run software which attempts 1 billion passwords per second, so this demonstrates just how feeble a password on its own is. Therefore, integrating MFA is crucial for establishing a strong set of defenses against potential security attacks.
Benefits of Multifactor Authentication
Let’s take a look through the benefits that MFA can bring to your business:
- Physical credentials can’t be compromised by social engineering. Sure, it’s possible to get a password to someone’s bank account over the phone with a bit of trickery, but how are you going to talk someone out of their swipe card?
- Hackers are instantly repelled by MFA as their time is better spent on less complex systems to break into.
- MFA can be very cost effective if all it requires is for an employee to be sent an SMS message with a code.
- There’s an increase in awareness of security breaches e.g. if an employee receives an SMS message advising that a login attempt has been made, but they haven’t tried to login, then they can alert your IT department.
Considering Multifactor Authentication?
If you’re trying to make your mind up on MFA then let us confirm the answer for you: it’s essential for your most important data and emails! Anything which creates a headache for hackers is an excellent deterrent and MFA achieves this effectively.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More