 Ransomware is regularly in the news, so we’re beginning to understand it more. However, a new form of ransomware is now changing the landscape.
Ransomware is regularly in the news, so we’re beginning to understand it more. However, a new form of ransomware is now changing the landscape.
Bitcoin has always been the preferred payment method for releasing encrypted files following an attack, but the newly detected Kirk ransomware is not interested in Bitcoin payments. Instead, it’s demanding its ransom through the relatively new cryptocurrency known as Monero.
Now, ransomware is a troublesome piece of malware at the best of times, so if the hackers behind these attacks are changing tactics then it’s important to be aware of what’s happening. And that’s why I’ve decided to take a closer look at the Kirk ransomware to help eliminate any confusion.
Understanding Kirk

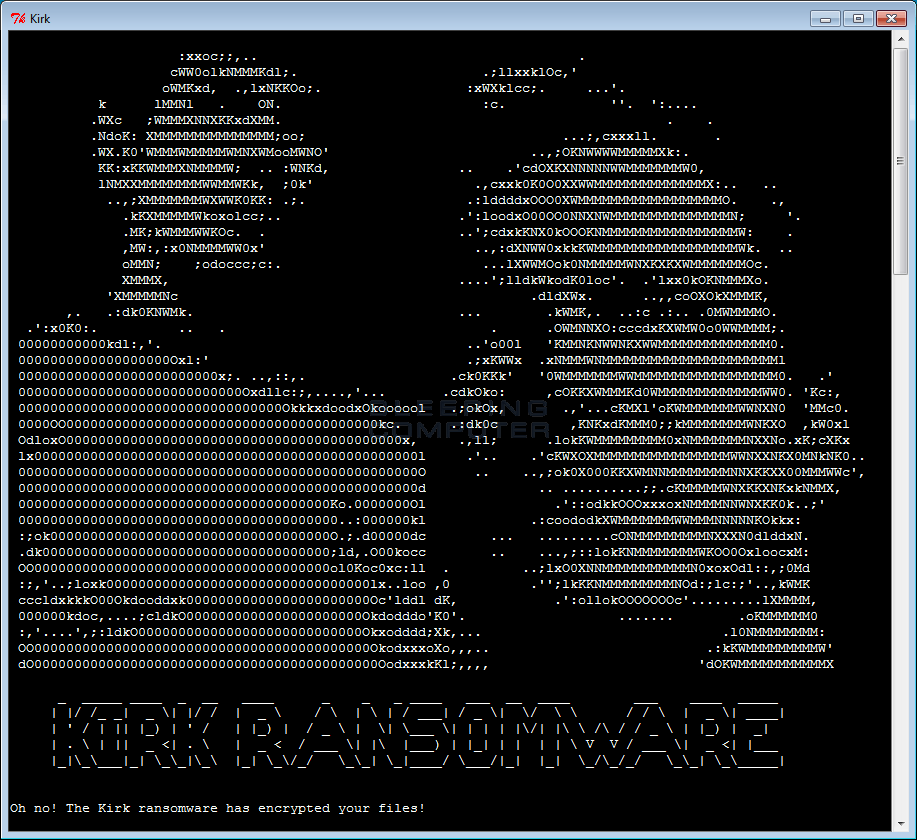
Kirk ransomware is a piece of malicious code which appears to be going about its business in the normal manner. Researchers believe that its preferred method of attack is to impersonate the network stress tool Low Orbital Ion Cannon (LOIC). Once the ransomware has been activated, Kirk gets to work by encrypting the user’s files – it’s currently believed that it targets a total of 625 different file types.
The target is unaware of what’s happening as all that happens is that a message box pops up which mimics the LOIC company slogan of “Low Orbital Ion Cannon | When harpoons, air strikes and nukes fail | v1.0.1.0”. Meanwhile, the files are being encrypted as the victim carries on with their daily activities. However, a ransom note is soon deposited into the same folder as the ransomware; this note is then displayed in a window for the victim to learn that a number of their files have been encrypted with the .kirk filename.
The only way to decrypt the files is by paying the ransom payment to the hackers. This, it is hoped, will facilitate the purchase of the Spock decryptor – note the Star Trek reference – but researchers are yet to get their hands on this decryptor to evaluate its validity as a solution. Now, the interesting thing about Kirk is that it demands its payment in Monero which is causing a whole host of new problems.
Bitcoin is a notoriously difficult currency to lay your hands on, you can’t just go down to the bank and expect the teller to exchange your dollars for Bitcoins. Instead, you need special merchants to trade your dollars and this isn’t particularly cheap or easy. However, where Kirk differs is that it’s requesting payment from an even more obscure monetary source, so this has the potential to leave victims completely baffled.
Combatting Kirk

At present, the Kirk ransomware hasn’t been cracked and there is no known rescue for encrypted files aside from making the payment. Therefore, it’s crucial that you take the following steps to avoid falling victim to the Kirk ransomware:
- Don’t activate untrusted macros that are embedded in Microsoft Office documents as this is how ransomware is usually activated.
- The only way to truly know if an Office document is genuine is by opening it but, to minimize the risk, try installing a Microsoft Office viewer as this will allow you to view it without macros.
- Provide annual training to your employees on malware and the many forms it can take. It’s a lack of knowledge which leads to people activating ransomware.
- Maintain regular backups of your files as this gives you some breathing space (and saves you the cost of a ransom) if your files do become encrypted.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More