One of the most common ways to protect your PC is by working with a firewall, but what exactly is a firewall and what can it do to protect you?
Protecting your organization’s PC network should be one of your main priorities when it comes to IT due to not only the amount of data being transferred, but also the impact that a security breach could have on your productivity. Thankfully, there are many security options available to help strengthen your defenses and one of the oldest forms of security is a firewall. And, despite the traditional nature of this defense, it remains one of the most effective for stopping intruders accessing your network.
To help you understand this area of cyber-security in a little more depth, we’re going to take a quick look at how a firewall works and why you need one.
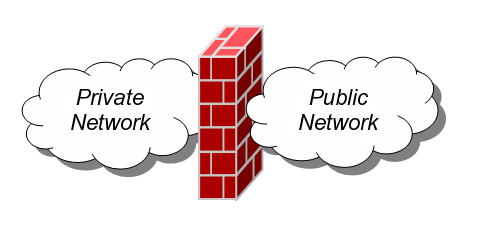
What is a Firewall?
The concept behind a firewall is a relatively simple one compared to other forms of cyber-defense with its main objective being to stop malware and malicious attacks penetrating a computer network. Essentially, a firewall is much like a content filter in that you’re able to define exactly what is allowed to both enter and leave your network. This filter is an automated process, so it’s possible to program the firewall to a highly tailored specification and then leave it to filter out anything deemed nonviable for the network.
What Exactly Can a Firewall Do?
A firewall, of course, is more than just a filter. In fact, fthere are a wide range of benefits that any organization can benefit from and these include:
- Internal Safety: Many security lapses come from internal actions taken by staff such as accessing malicious websites or downloading malicious email attachments. While these are almost always innocent mistakes, the ramifications can be highly inconvenient. With a firewall in place, however, these concerns can be significantly reduced due to the level of control at your disposal which includes restricting outgoing connections to specific websites and receiving emails with attachments known to be malicious.
- External Protection: As information filters in from the internet, firewalls are able to analyze this data and verify whether the data is safe to enter your network. The firewall does this by determining the location and source of the data and then authenticating it against a set list of permissions. This verification is incredibly quick and will almost instantly confirm whether this data is allowed through or needs to be rejected. And, given the amount of headlines attributed to cyber-attacks on business, this provides some highly valuable peace of mind.
- Monitoring Outgoing Data: One of the main draws of using a firewall is that they’re capable of analyzing data that leaves your organization. In particular, this is very useful in the IT world to monitor any unusual activity on your network. If, for example, a larger than usual amount of data is being transmitted to unfamiliar sources then there’s a good chance that your network has been hacked and is being used to orchestrate bot attacks. With a firewall in place, though, you can identify this process early on and work on shutting it down.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More